Security
A technical support case revealed a remote exploit of web-exposed spam quarantine management to gain root.

Cisco appliances and their virtual equivalents are being exploited via a CVSS 10 vulnerability in their spam management system, Cisco said.
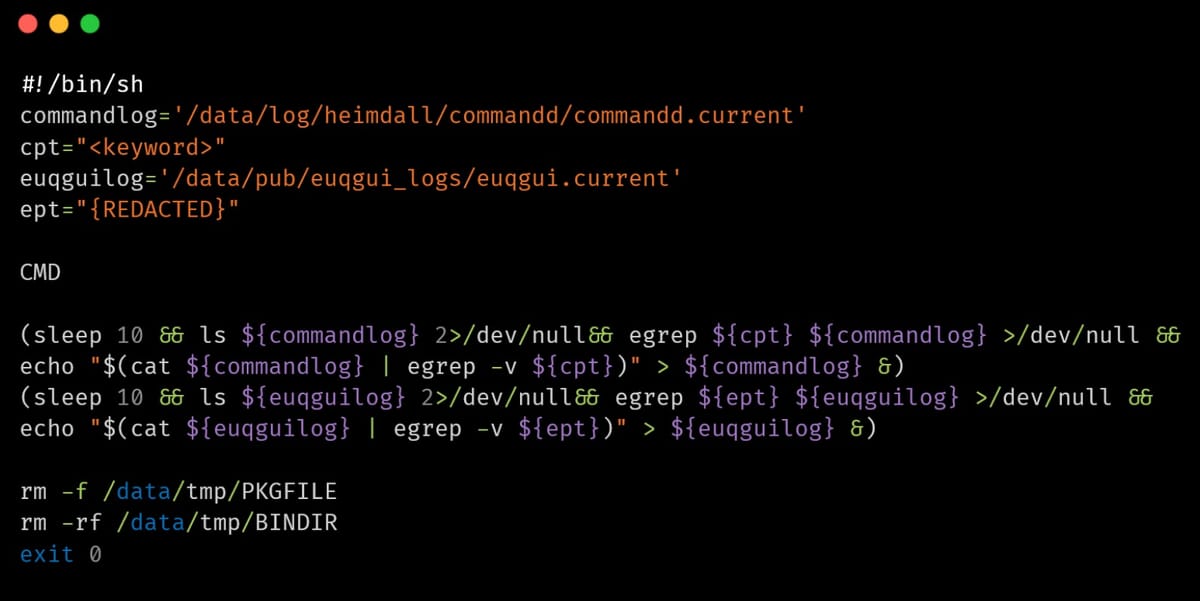
The vulnerability has been allocated CVE-2025-20393. There is no patch yet. Attackers are planting a previously unseen backdoor for persistence.
Cisco said became aware of the attacks on December 10 via a technical support request. They have been traced back to at least late November.
The affected appliances are Cisco's Secure Email Gateway, and the Secure Email and Web Manager, once known under the IronPort brand, across all versions of Cisco AsyncOS. Attacks require spam quarantine to be enabled – which it is not by default – and reachable from the internet, Cisco said.
The critical Cisco vulnerability is being used to plant a backdoor web server along with a set of tunnelling tools and a log purger. Cisco Talos said it has linked the campaign to "a Chinese-nexus advanced persistent threat" it designated UAT-9686 by way of tooling and tactics.
Cisco said its Secure Email Cloud products are not affected, and it is "not aware of any exploitation activity against Cisco Secure Web".
Mitigation is by way of the usual filtering and hardening – and Cisco recommended changing the default administrator password.
UAT-9686 is "pretty good at what they do", said security researcher Kevin Beaumont, linking the group to attacks on the Cisco Adaptive Security Appliance (ASA) discovered in November, as well as CitrixBleed.
Cisco has IOCs seen to-date here.
More details to follow.