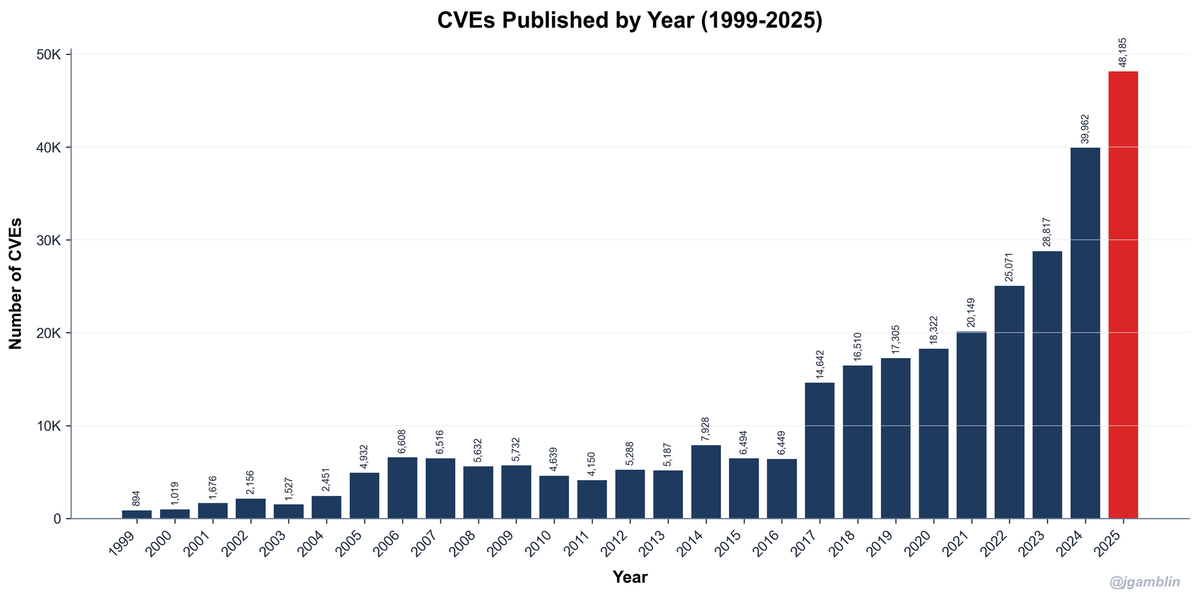
A record 48,185 CVEs were published in 2025.
They included over 8,000 cross-site scripting (XSS) bugs – a vulnerability type known for decades and easily avoided, e.g. via HTML sanitisation.
Analysis by Cisco’s Jerry Gamblin shows that 3,984 of the CVEs (designations for known cybersecurity vulnerabilities in software) were rated critical.
In terms of the products against which most CVEs were allocated, the Linux kernel dominated, followed in second place by Windows 10, then Android, Adobe’s Experience Manager, and Apple’s MacOS, in the fifth spot.
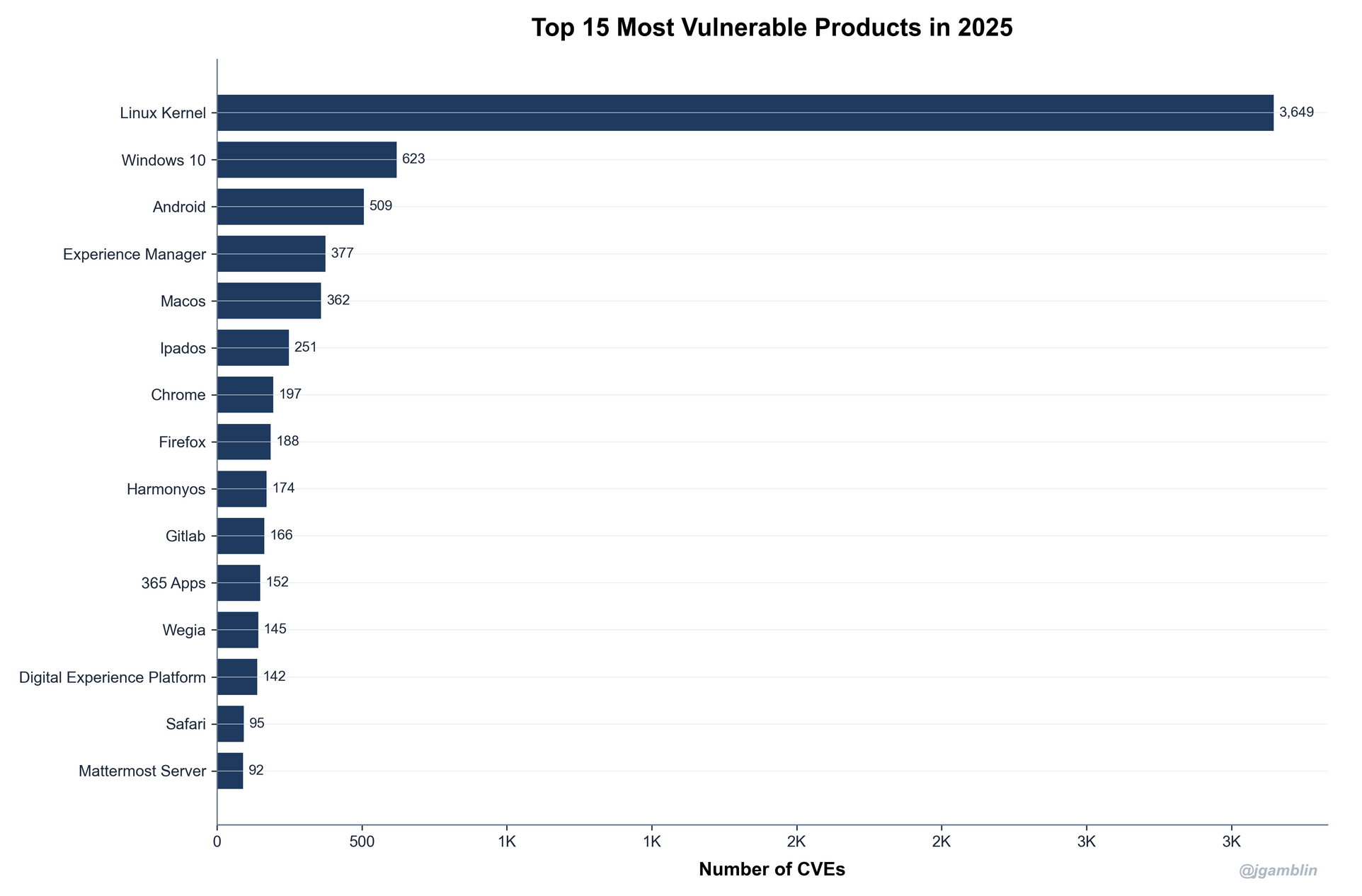
(High numbers of CVEs can be because “many eyeballs make all bugs shallow” and/or a sign of mature security programs designed to spot, or incentivise the spotting of, security flaws; e.g. via bug bounty programs.)
Also notable, Gamblin highlighted, was that “the CVE Numbering Authority ecosystem has shifted dramatically. In previous years, major software vendors dominated this list. In 2025, we see the ‘WordPress Effect.’
2025's CVEs: Wordpress shops drive volume
Patchstack and Wordfence (dedicated to WordPress plugin security) are “now top drivers of CVE volume. Patchstack (#1) alone assigned 7,007 CVEs, vastly outnumbering traditional giants like Microsoft (#6) or Google. This reflects the intense scrutiny on the third-party plugin ecosystem,” he wrote.
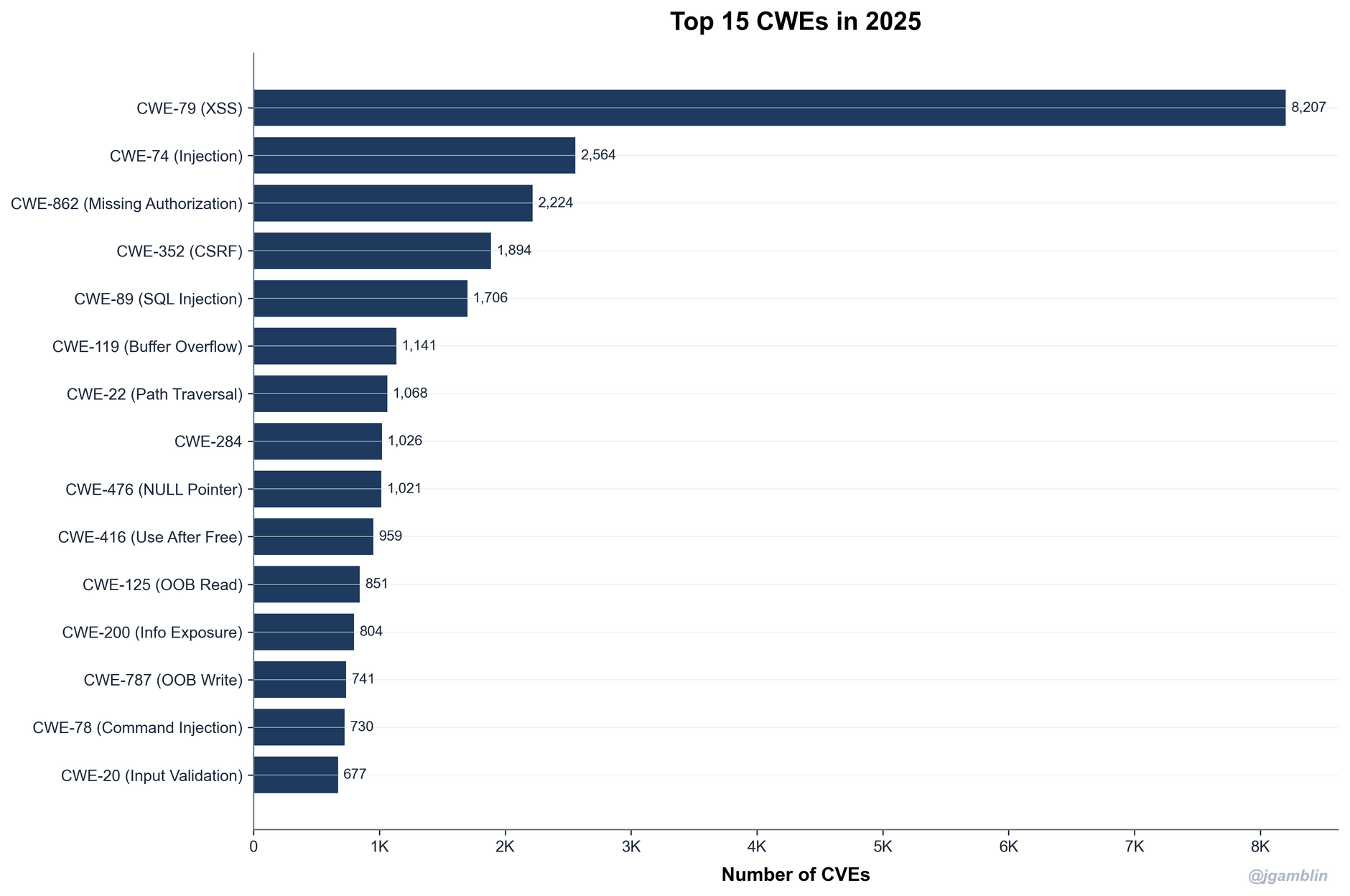
The number of XSS bugs stems mostly from “Wordpress plugins and older vulnerabilities,” noted security researcher Patrick Garrity, suggesting that future CVE growth is likely to be “highly dependent on a handful of high volume CNAs that largely triage vulnerabilities in third party software.”
It also arguably reflects a persistent problem with developers writing insecure code and too few organizations being on top of this. Chris Reddington, a senior program manager in DevRel strategy at GitHub, cites its native tools like code scanning, dependency review, and Dependabot as there to help "teams detect and mitigate issues early, directly as part of their lifecycle."
He adds: "As AI becomes increasingly integrated into development (and projected to assist in writing the majority of code within the next five years), developers need to pair automation with thoughtful oversight, using AI assertively whilst combining that with the foundations of quality checks, patterns and practices that we already use today..."
Asked by The Stack whether the strikingly high numbers of CVEs – including for highly specific platforms – meant that they had diminishing utility for defenders, Garrity said that those for the likes of Wordpress could be easily filtered out of feeds – whilst noting that he would like to see the “CVE program evolve with better data quality, accountability and overall program management,” after a highly challenging few years for NIST’s NVD program.
Open-source bugs
A notable trend in the past 18 months has been the way in which LLMs speed up the ability of security researchers to develop exploits in minutes, drawing on code from public fixes (PRs) for open-source projects.
(As reported by The Stack, publicly exploited bugs in LangFlow and MongoDB in 2025 both saw AI-augmented exploit/POC development.)
That has left many security researchers highlighting the importance of tracking upstream fix activity in the open-source world, as well as CVEs: Databases like GHSA (which pulls in GitHub-originated security advisories from the world of open source software) and/or OSV help here.
As Garrity notes, “open source pURL identifiers make a lot of sense.
But despite the CVE programs’ many shortfalls and associated turf wars (CVE.org is part of the Department of Homeland Security. NVD, which pulls CVE data and enrichens it, is part of the Department of Commerce) it is still the “primary source for universal vulnerability identification” he concluded.
CVE program: MITRE to get renewed funding?
Close industry watcher Tom Alrich meanwhile says he expects CISA to renew CVE.org’s contract to run its part of the program in March.
He wrote on January 4: “A lot of people in the vulnerability management community have been upset with the CVE Program for years because of numerous problems like a) missing information in many CVE records (especially CVSS scores and CPE names), b) inaccurate or missing product, vendor and version information, c) lack of machine-readable version range information, etc. They complain that, when they bring problems directly to the CVE Program, they either don’t get any response or they’re simply told the issue has been noted and will be addressed when time permits – but time never seems to permit, since they never hear anything more about it.
“Unfortunately, these people don’t seem to understand the First Law of Government Contracting: A contractor never agrees to undertake more work than what is specifically required by their contract – that is, unless the agency that approved the contract is willing to sign a Change Order and send it over, accompanied by a fat check…”
