
SaaS and technology firms are being explicitly targeted by a Chinese APT that is backdooring network appliances and maintaining deep persistence – the average dwell time is 393 days, warned Mandiant on Thursday.
Using malware dubbed BRICKSTORM by Mandiant, the highly stealthy threat group is using its access to gain "data to feed development of zero-days and establishing pivot points for broader access to downstream victims,” it said.
The threat group, tracked by Mandiant as UNC5221, persistently targets VMware vCenter and ESXi hosts, post-compromise. TTPs are here.
John Hultquist, Chief Analyst, Google Threat Intelligence Group, warned that he anticipates many organisations “who actively [threat] hunt [will] find that this actor has been active in their networks for some time.”
- Mandiant has a regex-based utility for threat hunting here.
- Nextron Systems’ Florian Roth has Yara rules here.
Edge devices like firewalls, VPN servers, routers and email servers have become a major target of attackers. they often have direct connections to the internet, are typically not supported by endpoint detection and response (EDR) software, and can be exploited to pivot deeper into enterprise networks.
BRICKSTORM: Initial access obscure
UNC5221's use of post-exploitation scripts to “obscure entry” and length of average dwell time means Mandiant has struggled to establish the initial access vector, but the “available evidence points to the actor's focus on compromising perimeter and remote access infrastructure,” it said.
The incident response specialist’s team did not name any particular flavour of targeted network appliance nor potential CVE exploited in this week’s report, but first cited BRICKSTORM use in an April 2024 write-up on Ivanti appliance exploitation. (Via CVE-2023-46805, CVE-2024-21887, CVE-2024-21893 and CVE-2024-21887.)
See also: Ivanti CEO promises product security overhaul, enhanced bug bounties after shocking analysis
Chinese hackers previously compromised over 20,000 Fortinet devices in 2022-2023, breaching “a large number” of defense industry firms. They exploited a previously unseen, bespoke malware for Fortinet devices dubbed COATHANGER that “survives reboots and firmware upgrades.”
In July 2025 meanwhile the French government warned that a China-based APT tracked as UNC5174 had exploited three Ivanti bugs to breach government targets.
BRICKSTORM malware: Post-exploit activity
Mandiant described BRICKSTORM last year as a “Go backdoor targeting VMware vCenter servers. It supports the ability to set itself up as a web server, perform file system and directory manipulation, perform file operations such as upload/download, run shell commands, and perform SOCKS relaying” and communicates over WebSockets to a hard-coded C2.
In at least two cases, the threat actor used their access to vCenter to clone Windows Server VMs for key systems such as Domain Controllers, SSO Identity Providers, and secret vaults. This is a technique that other threat actors have used.
With a clone of the virtual machine, the threat actor can mount the filesystem and extract files of interest, such as the Active Directory Domain Services database (ntds.dit). Although these Windows Servers likely have security tools installed on them, the threat actor never powers on the clone so the tools are not executed" - Mandiant
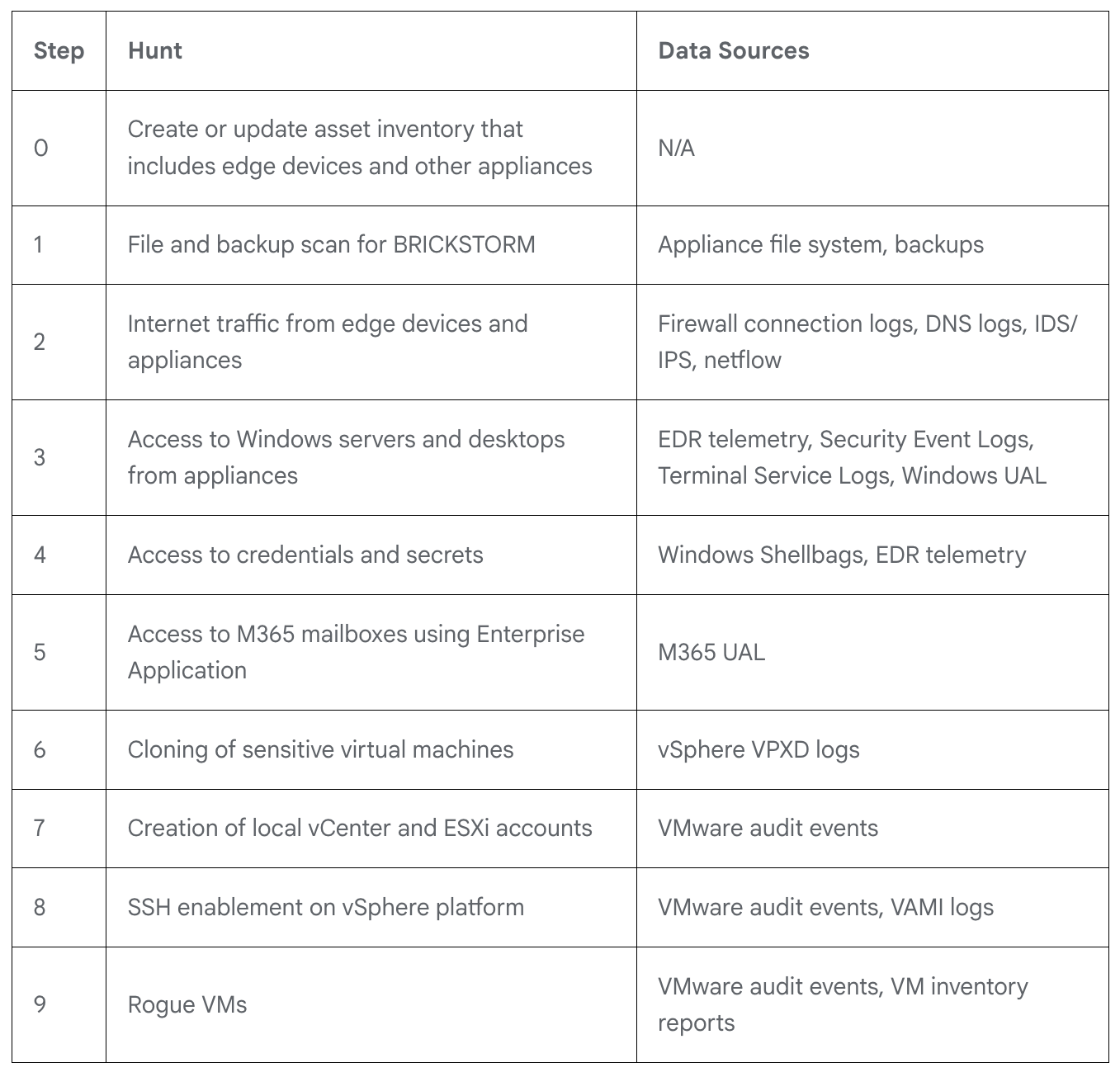
Traditional “atomic” IOCs are of little use in threat hunting said Mandiant: “No reuse of C2 domains or malware samples… coupled with high operational security, means these indicators quickly expire or are never observed at all.” It proposed a “minimal set of hunts” in the graph above.
