
Oracle has pushed a fix for a trivially exploitable CVSS 10 bug that has the potential to impact a wide range of Oracle software environments.
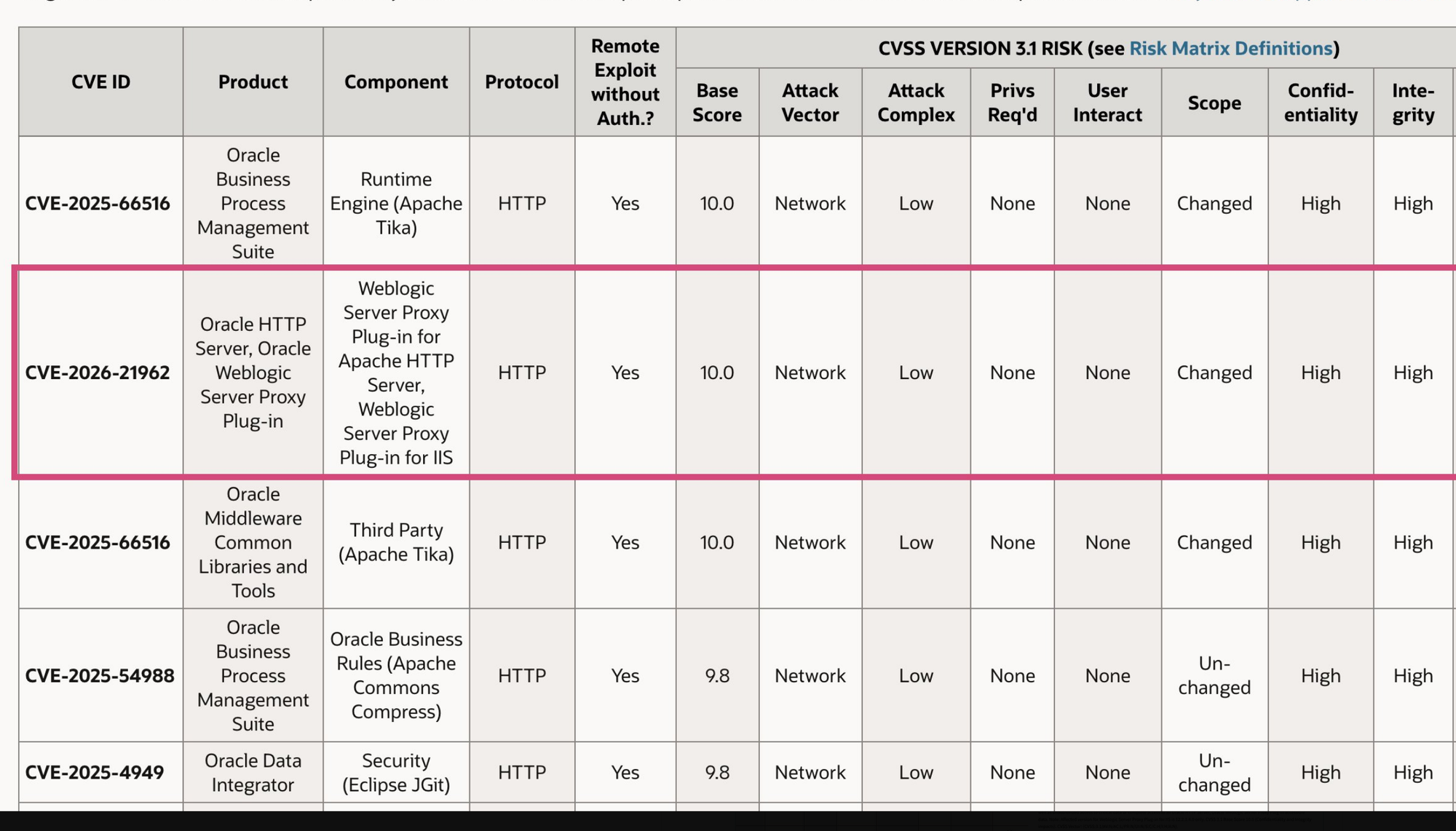
The vulnerability, allocated CVE-2026-21962, affects Oracle HTTP Server and a pair of WebLogic Server plugins – and gives a remote, unauthenticated attacker potentially deep access to Oracle’s Fusion Middleware.
An attacker merely needs to send a specially crafted HTTP request to the affected exposed server to access target systems, security researchers said.
No confirmed proof-of-concept (POC) exploit was available as The Stack published and exploitation had yet to be seen in the wild, but both are highly likely to follow in short order. The bug is in the following:
- Oracle HTTP Server version 12.2.1.4.0, 14.1.1.0.0, and 14.1.2.0.0
- Oracle WebLogic Server Proxy Plug-in version 12.2.1.4.0, 14.1.1.0.0, and 14.1.2.0.0
- Oracle WebLogic Server Proxy Plug-in for IIS version 12.2.1.4.0
Per cybersecurity firm Purple Ops: “This [malicious HTTP] request bypasses existing security controls, allowing the attacker to execute unauthorized operations. The nature of the flaw allows for a total takeover, which includes the ability to create, modify, or delete any data within the system.
Purple Ops added: “Because the proxy plug-in sits between the public-facing internet and the internal application logic, a compromise at this level provides a foothold for lateral movement into the internal network…”
(Oracle Fusion Middleware environments often rely on the Oracle HTTP Server and WebLogic Server Proxy Plug-in to forward web traffic into backend application servers – and are potentially vulnerable as a result.)
This is how Oracle itself got popped...
Oracle itself was hacked in 2025 via an unpatched Fusion Middleware instance; security researchers say likely via exploitation of a 2022 bug affecting its OpenSSO Agent that lets an “unauthenticated attacker with network access via HTTP compromise Oracle Access Manager."
When reporting on that vulnerability (CVE-2022–21445) back in 2022, The Stack revealed that despite its criticality and easy exploitability, Oracle did not push a fix for six months after two Vietnamese security researchers disclosed it to the software company via the ZDI bug bounty programme.
The security researchers in question told us at the time that they resorted to breaching a vital Oracle domain using the exploit in an effort to drive home its severity, after failing to get a response – and that Dell and Starbucks had been among those with exposed systems at the time.
CVE-2026-21962 is one of numerous critical vulnerabilities given fixes under Oracle’s monster quarterly patch cycle. This week’s set of fixes includes 337 security updates for 158 unique CVEs across 30 Oracle product families.
