
Customers of Sitecore, a widely used provider of software deployed by Fortune 500 firms, are being hacked after some of them used a machineKey publicly available since 2017 to secure their software.
Sitecore, a Gartner Magic Quadrant “visionary” for Digital Asset Management, names Bayer, Canon, HSBC, L'Oréal, Michelin, NTT, United Airlines, and Zurich Insurance among its many blue chip customers.
A loose Shodan search suggests over 20,000 exposed instances.
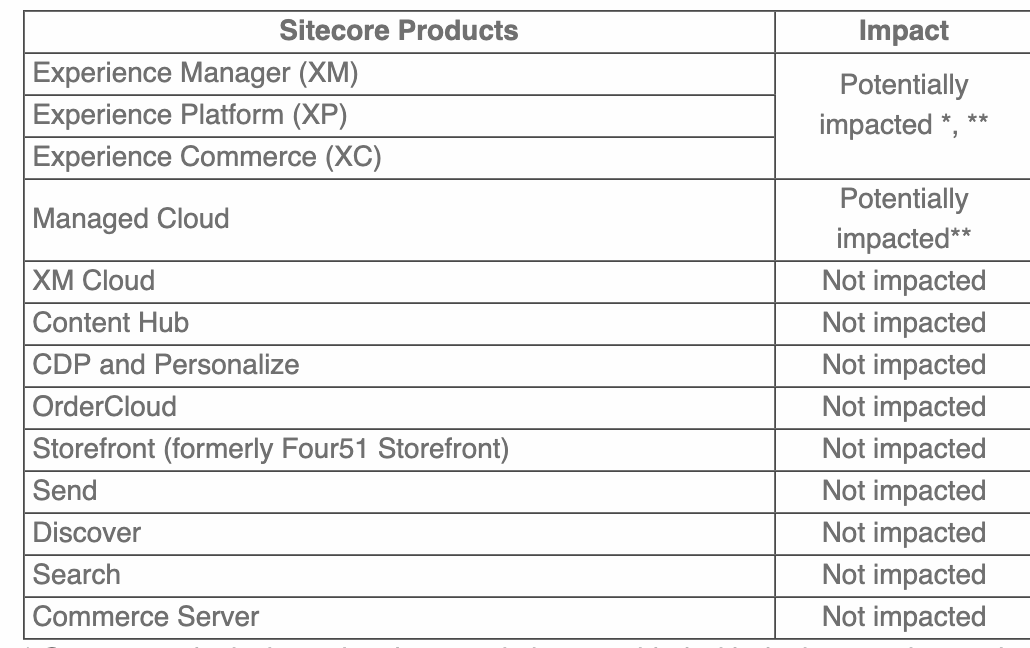
Zero day exploitation of the Sitecore misconfiguration/bug was spotted by Mandiant, which said on September 3 that it affects customers who deployed any version of multiple Sitecore products (“specifically Sitecore XP 9.0 and Active Directory 1.4 and earlier versions”) using a sample key “exposed in publicly available deployment guides for the firm’s software.”
The critical (CVSS 9.0) vulnerability, now allocated CVE-2025-53690, is simply the result of Sitecore users “copying and pasting example keys from official documentation, rather than generating unique, random ones – a move we don't recommend,” watchTowr’s Ryan Dewhurst said drily.
The security firm’s head of threat intelligence added: “Any deployment running with these known keys was left exposed to ViewState deserialization attacks, a straight path right to Remote Code Execution.”
The keys in question are machineKeys that allow the application to encrypt or hash sensitive data, such as authentication cookies. Mandiant said that Sitecore has confirmed fresh software deployments now automatically generate a unique machinekey to avoid this happening.
Existing customers, meanwhile, will want to threat-hunt.
What do I do?!
Sitecore says that customers who “deployed any version XM, XP, XC topologies and who followed the deployment instructions provided with XP 9.0 or earlier and Active Directory 1.4 or earlier and used the sample machine key (for example, machine key: BDDFE367CD..., validation key: 0DAC68D020...) are vulnerable and should immediately follow Sitecore guidance including:
- Examine their environment for suspicious or anomalous behaviour.
- Rotate the machines keys within web.config file.
- Ensure any system <machineKey> elements in web.config files are encrypted.
- Restrict web.config file access to application administrators only.
- Take timely action to implement the practice of rotating static machine keys.”
Mandiant has a Yara rule and IOCs.
What are the Sitecore attackers doing?
A detailed threat report by Mandiant, which conducted incident response for one Sitecore customer, showed that the threat actor had maintained persistence through a combination of methods, and was spotted using both created and compromised administrator credentials for RDP access.
The attacker appears to have used Go-based token-stealer GoTokenTheft to identify and steal all unique user tokens active on the system. They also deployed the open-source EarthWorm tunneller; a “reconnaissance tool designed to gather system, network, and user information” that Mandiant tracks as WEEPSTEEL; and “disabled password expiration for administrative accounts…” for persistence among other techniques.
As Gartner notes, DAM platforms like Sitecore’s can often be found serving “every part of the organization, including marketing, sales, HR, technology, manufacturing, legal, finance, call and service centers, third-party suppliers, agencies and distributors” – a goldmine for hackers.
Attack surface management firm watchTowr has previously prodded and poked Sitecore’s software to assess its security and found it lacking – the company has recently patched several other pre-auth RCE vulnerabilities.
