Russian cybersecurity company Kaspersky says several iPhones on its corporate network were hacked using an iOS zero day – with the zero click campaign launched in 2019 and ongoing. Kaspersky is still analysing the final payload but said the code is run with root privileges and “can run arbitrary code downloaded as plugin modules from the C&C server.”
Kaspersky did not attribute the attack, which it detailed along with a clutch of indicators of compromise on June 1. But Russia's FSB security agency claimed in a short note this week that “thousands” of iPhones had been infected not just within the Russian government but “staff from the embassies of Israel, China, and several NATO member nations in Russia.”
Kaspersky iPhones hacked: FSB points to NSA
It provided no details on the campaign nor evidence but alleged that the attacks were the result of “close cooperation” between US intelligence and Apple – the latter responding that “we have never worked with any government to insert a backdoor into any Apple product and never will.”
Leaks by former NSA contractor Edward Snowden suggested that the NSA’s PRISM programme facilitated data collection “directly from the servers” of US technology providers including Apple, whilst further leaks provided details on an NSA “software implant for the Apple iPhone that utilizes modular mission applications to provide specific SIGINT [signals intelligence] functionality” that “includes the ability to remotely push/pull files from the device. SMS retrieval, contact list retrieval, voicemail, geolocation, hot mic, camera capture, cell tower location, etc.”
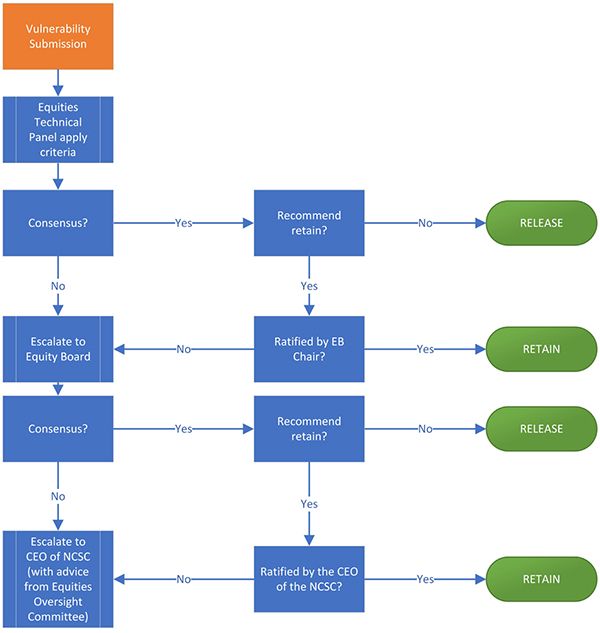
Intelligence services, everywhere, aim to hold on to carefully chosen and strategically useful exploitation capabilities over widely used software. Indeed, the UK’s GCHQ has helpfully spelled out precisely why and when it chooses to do that, rather than to disclose vulnerabilities to vendors.
Kaspersky said of the current campaign: “The single most reliable indicator that we discovered is the presence of data usage lines mentioning the process named ‘BackupAgent’. This is a deprecated binary that should not appear in the timeline during regular usage of the device.
“It is important to note that there is also a binary named ‘BackupAgent2’, and that is not an indicator of compromise. In many cases, BackupAgent is preceded by the process ‘IMTransferAgent, that downloads the attachment that happens to be an exploit, and this leads to modification of the timestamps of multiple directories in the ‘Library/SMS/Attachments’.
"The attachment is then deleted, leaving only modified directories, without actual files inside them." (See Kaspersky's full writeup here.)
The cybersecurity company said that the most recent version of the devices successfully targeted is iOS 15.7 but "given the sophistication of the cyberespionage campaign and the complexity of analysis of iOS platform, we can’t guarantee that other versions of iOS are not affected."









