News
There are no workarounds that remove the vulnerability, which allows unauthenticated remote command execution on vulnerable systems. A patch is available.

Goldman Sachs CIO says "there’s a great opportunity for capital to move towards the application layer, the toolset layer. I think we will see that shift happening..."

"We’re starting to see multimodal AI models, and I think one modality that hasn’t been fully exploited yet is that of the time series. This would be using AI to deal with data points attached to a particular timestamp..."

MI5 is off to the cloud; GCHQ is ramping up Computer Network Exploitation capabilities; MI6 needs cultural changes to get a new IT platform running smoothly...

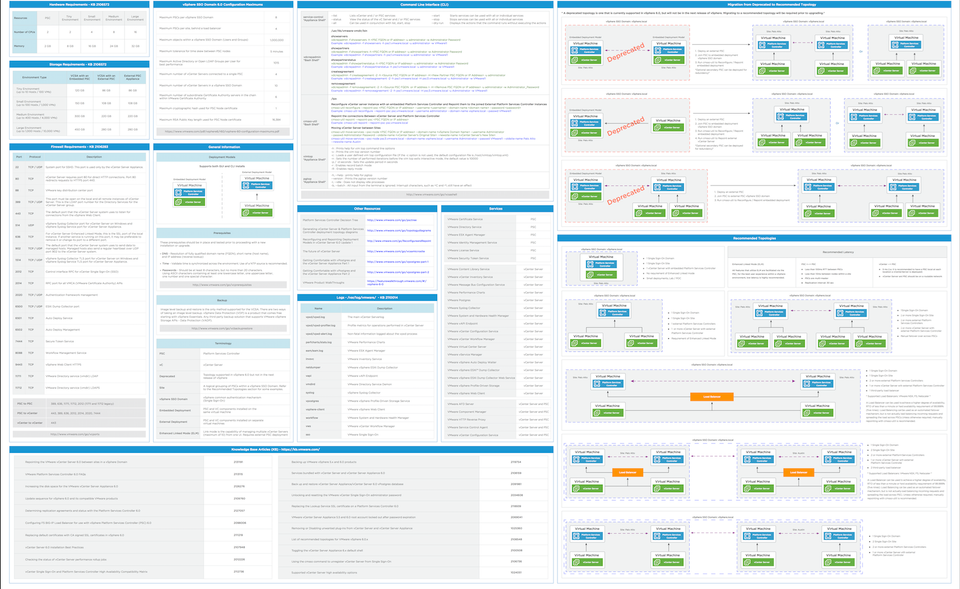
Goodbye vSphere Hypervisor. Goodbye Aria Operations. Goodbye NCX. Goodbye HCX. Goodbye more acronyms than we know what to do with; though Broadcom does; at least as standalone SKUs...

Stateful. A Web UI. Customisable plugins. Six LLMs supported. Nice work, Microsoft.

Clumsily or coldly firing staff? Be prepared for prime time on social media...

VPN appliances "all appear to have been constructed with the code equivalent of string, stamped with the word ‘secure’ and then just left to decay for 20 years..."
