vulnerabilities

POCs for CVSS 10 bug are out of the bag, tens of thousands are exposed, and telemetry mitigation didn't work.
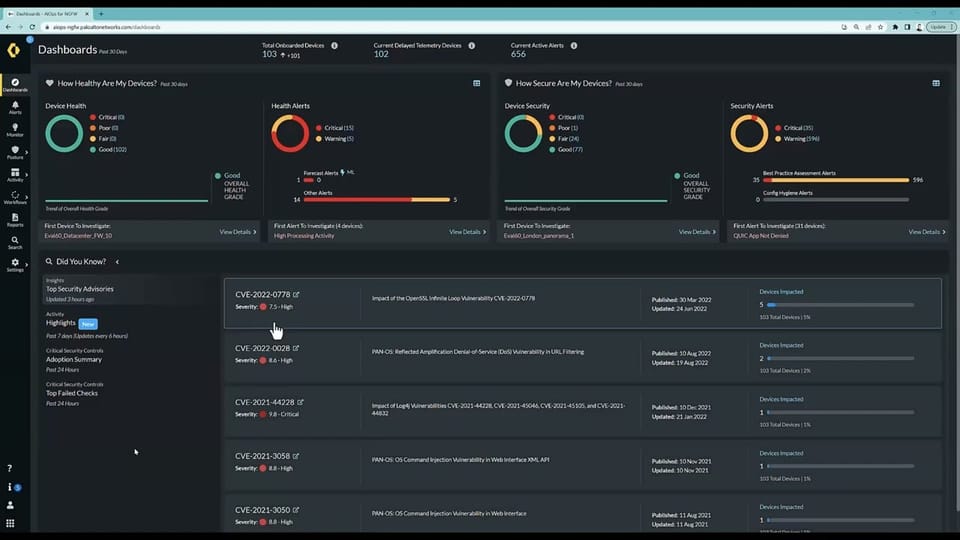
Patch? You'll need to wait until Sunday. Turn off telemetry (no, really; it's a mitigation!) and go to the pub. OK, maybe don't.

Incident suggests a state actor exploiting overstretched maintainer of an "unpaid hobby project"

A newly-discovered Linux bug could allow for password leaks. Worse yet, it has sat undiscovered in the OS for the last 11 years

JetBrains' platform "a suitable vector to position an attacker to perform a supply chain attack" if compromised warns Rapid7.

"The executable in question was built using the LockBit 3 ransomware builder tool leaked in 2022, so this particular sample may not have originated with the actual LockBit developers"


