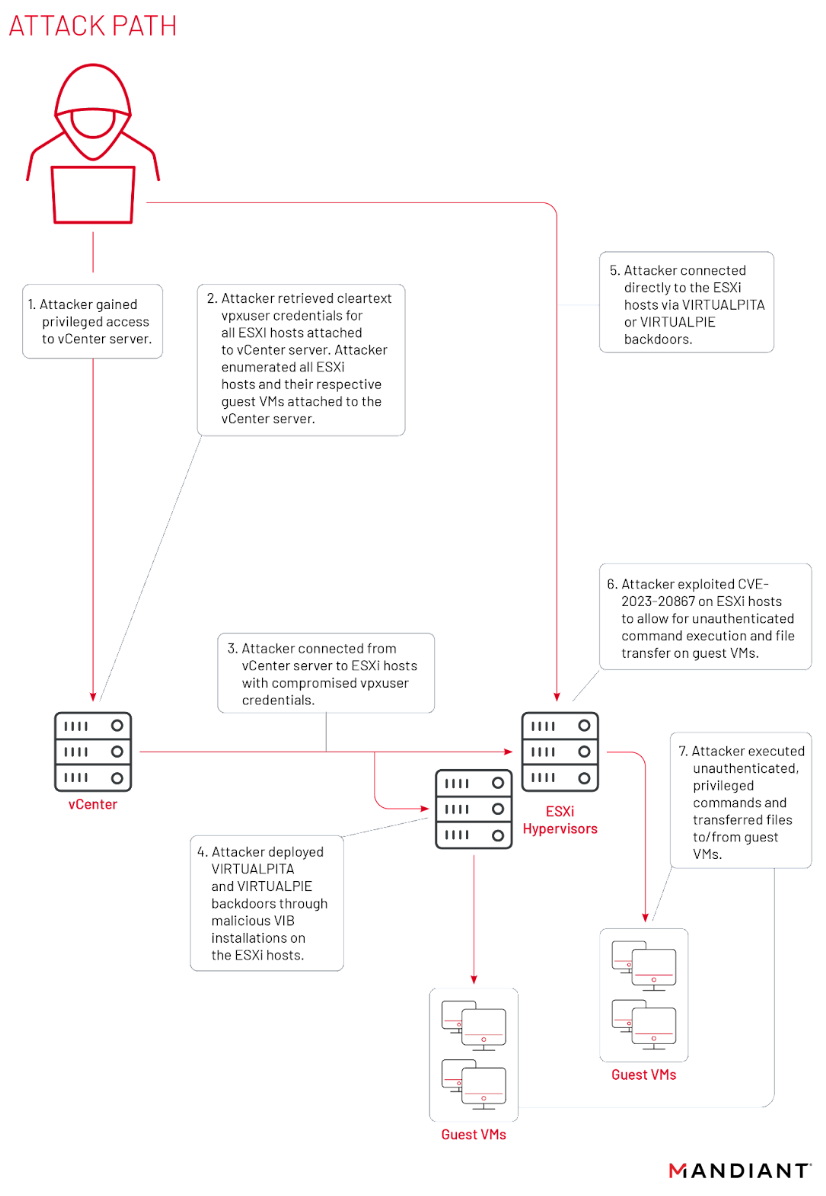
Mandiant says a VMware zero day affecting ESXi hypervisors and now allocated CVE-2023-20867 is being exploited by a Chinese APT to gain comprehensive lateral movement capabilities across VMware environments without leaving a trail or any logs of their activity.
CVE-2023-20867 requires initial access to exploit, but then let the cyber espionage threat group use it to “execute commands and transfer files to and from guest VMs from a compromised ESXi host without the need for guest credentials [and without generating] an authentication log event on the guest VM when commands are executed from the ESXi host.
Mandiant tracks the APT as “NC3886” and said that it has targeted defence, technology and telecommunications companies and has a track record of identifying and exploiting zero day vulnerabilities in firewall and virtualization technologies, which do not support EDR (antivirus et al.)
The VMware zero day, CVE-2023-20867, is just one of several tools used by the highly sophisticated (a word bandied about to frequently in incident response reports, but which seems to genuinely apply here) threat group – which also used a wide range of attacker scripts to get vpxuser credentials, enumerate ESXi hosts and their guest VMs, and manipulate connected ESXi host firewall rules in order to steal data.
These included use of a privilege escalation vulnerability, CVE-2022-22948, first identified and reported by Pentera Labs’ security researcher, Yuval Lazar, in 2022 which and at the time impacting more than 500,000 appliances running default vCenter deployments.
(As Lazar noted in her write-up on CVE-2022-22948 at the time: “Once compromised, the ease and convenience that vCenter offers for managing virtualized hosts in enterprise environments [plays into an] adversary’s hands, providing centralized access and widespread damage.”)
In a deep dive into what it found when investigating exploitation of this VMware zero day, Mandiant expressed respect for the “deep understanding and technical knowledge of ESXi, vCenter and VMware’s virtualization platform” held by the threat group – adding that the “retroactive cleanup performed within days of past public disclosures on their activity indicates how vigilant they are…Organizations must.. ensure that they’re not only monitoring their network at the operating system layer, but also continue to patch, maintain, and monitor the appliances that are running the underlying infrastructure” Mandiant concluded.
VMware published a security advisory with patches June 12. A spokesperson told The Stack: "The security of our customers is a priority at VMware. Today we released a security advisory to help customers apply the software updates to address CVE-2023-20867, a vulnerability that cannot be exploited unless the attacker has already gained root access. In addition to patching, customers are encouraged to take a holistic security approach that includes the hardening guidance available in our vSphere security blog.









