"An unmatched view of physical supply chain patterns, seasonal demand shifts and emerging trade corridors"
Security
|
Sep 18, 2025
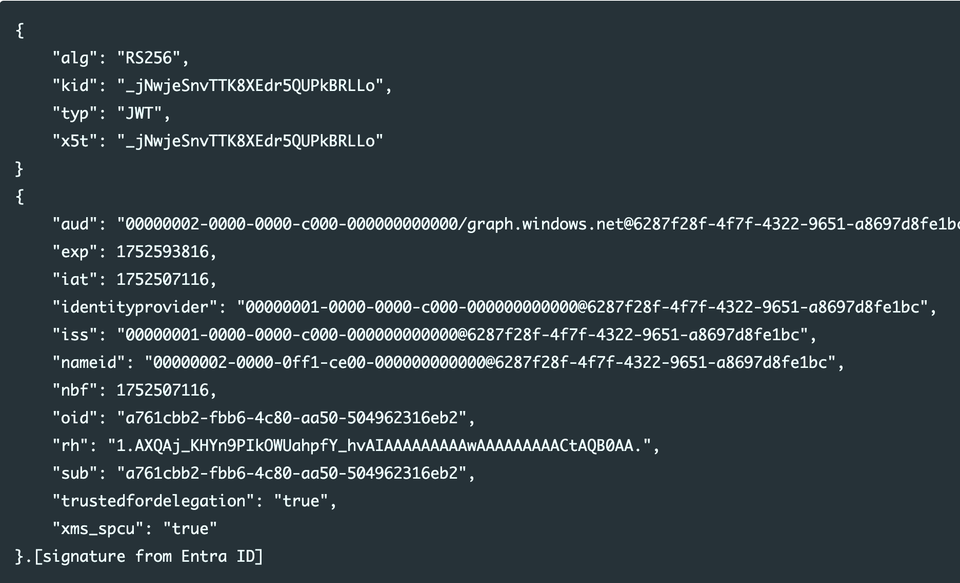
"I could authenticate as any user, including Global Admins, in any other tenant"

Trillion-dollar industry can't even measure its biggest problem -- "calibration" not the answer, says OpenAI
AI
|
Sep 05, 2025

"This landmark settlement far surpasses any other known copyright recovery. It is the first of its kind in the AI era