The Stack

Michael Cole, CTO of the European Tour group, points to importance of private 5G, as HPE rolls out solar-powered

Rapidly growing company had struggled to find the perfect CTO fit after co-founder Eliot Horowitz's departure.

“Given the model’s imperfect but increased proficiency for such tasks, it could appear to be useful for certain dangerous tasks...such as synthesis of certain illicit chemicals”

Willingness to stack racks with 30 pounds of kit and get a Red Hat Certified System Administrator certification welcomed.

The interoperability of shipping containers revolutionized the movement of goods across continents. This is what global digital mapmaking needs today.

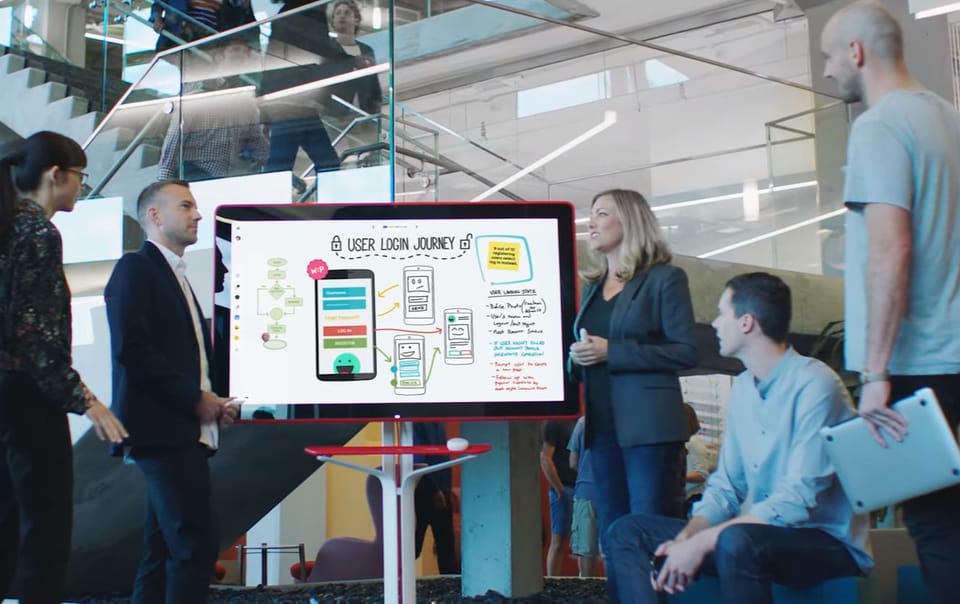
"I think our biggest challenge was, and this is something we learned the hard way, was the password reset..."