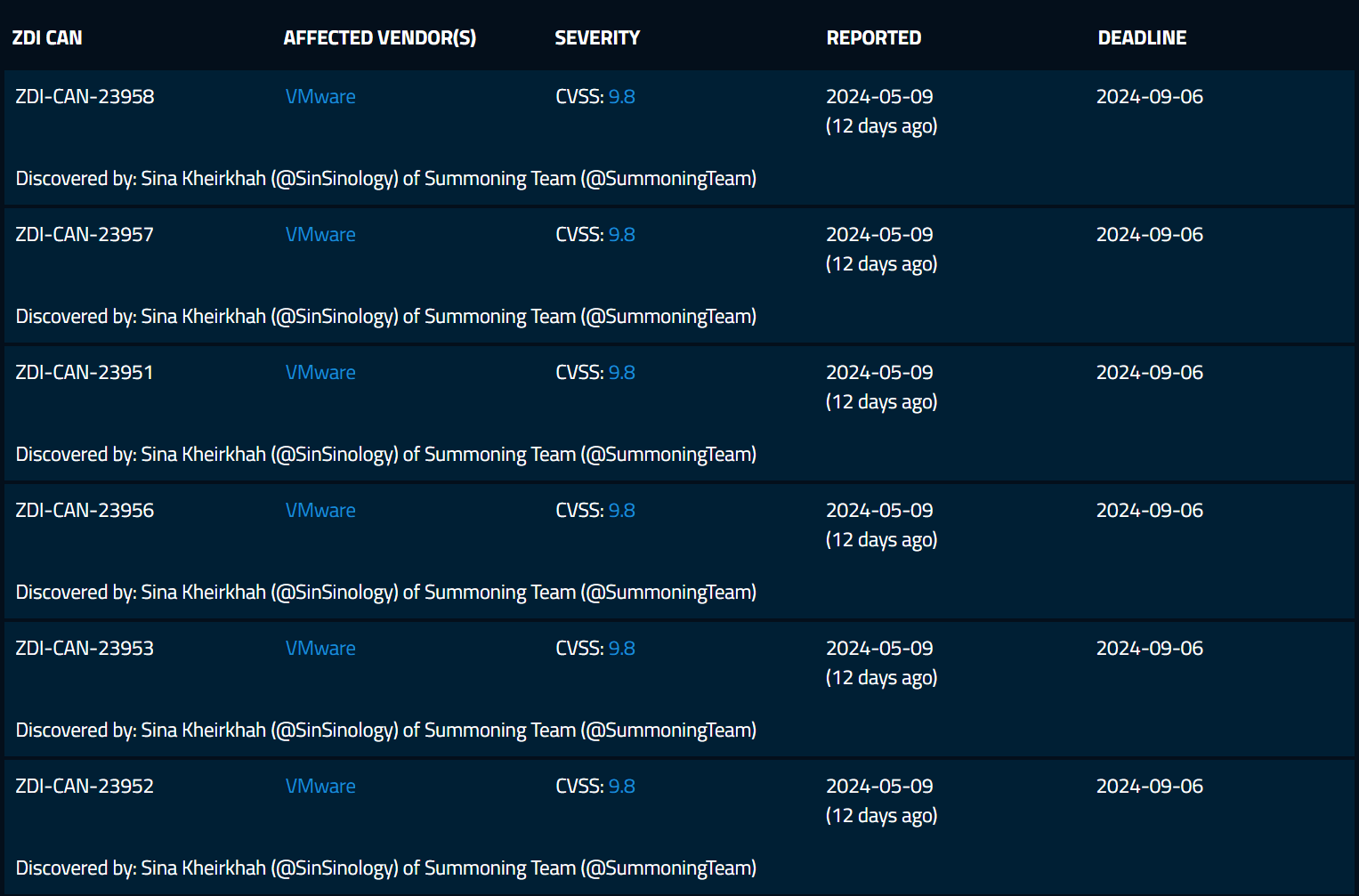
There are six critical new vulnerabilities in the default configuration of a widely used product from VMware that give root – but the company has not responded to outreach from the security researcher who found them.
The pre-auth RCE VMware vulnerabilities were found by prolific and respected security researcher Sina Kheirkhah, who told The Stack that prior to VMware’s buyout by Broadcom he has always had a swift response from its security team – but this time got nothing but crickets.
After 30 days of trying to rouse VMware the researcher, aka @sinsinology on X, took the vulnerabilities to bug bounty programme the Zero Day Initiative (ZDI) instead – which he said “took care of the issues and validated their severity within a matter of hours, not even days.”
They have now been validated as having a severity of CVSS 9.8.
The ZDI has given VMware until September 6 to respond with a fix and a bounty. If it does not get a response, it flags them as zero days and develops detection signatures for ZDI/Trend Micro customers.
The security researcher, @sinsinology declined to share any vulnerability details with The Stack out of concern that this could give a clue to threat actors looking to weaponise exploits – other than saying bluntly that the product is “always vulnerable to all six exploits, no configuration needed, no ports need to get opened; just straight-up RCEs, no fuss, no muss.”
They added that the VMware “bug types are [both] single issues and chains, but nowadays, given how sophisticated threat actors getting, giving out the bug class, even a single hair of a clue allows them to do things like patch diffing to get to the point; the devil is in the detail…”
See also: VMware evicted from Treasure Island: Nutanix hits jackpot with CIO
He said he contacted VMware from April 9 by email and again via X DM where he previously liaised with its security team, but got no response.
Triaging security disclosures is difficult, but @sinsinology’s previous CVEs with VMware include CVE-2023-20888 and CVE-2023-20889 (critical command injection vulnerabilities in Aria Operations for Networks) and a critical RCE exploit for VMware Cloud Foundation (NSX-V) via an XStream open source library vulnerability (CVE-2021-39144). VMware’s security team, he said, used to be responsive prior to its takeover by Broadcom.
Customers should cross their fingers that these get a patch soon; mitigate promptly if/when VMware publishes security advisories and meanwhile RTFM on VMware environment hardening. Patches, when they land, will no doubt be swiftly reverse-engineered by threat actors as VMware’s centrality to so many enterprise environments makes it a juicy target.
Ten weeks ago meanwhile VMware pushed fixes for a range of critical vulnerabilities in ESXi, Workstation, Fusion, and Cloud Foundation initially identified in China's 2023 Tianfu Cup Pwn Contest.
Details are here.
The Stack has contacted VMware for comment, but honestly since the takeover we've not had any joy getting responses either.
We look forward to updating this if we are pleasantly surprised.









