A critical vulnerability affecting over 50 products from RUCKUS Networks is being exploited in the wild. The company did not register a CVE, despite apparently knowing of the issue before it was reported to them by a security researcher. Its products are now being weaponised by a botnet.
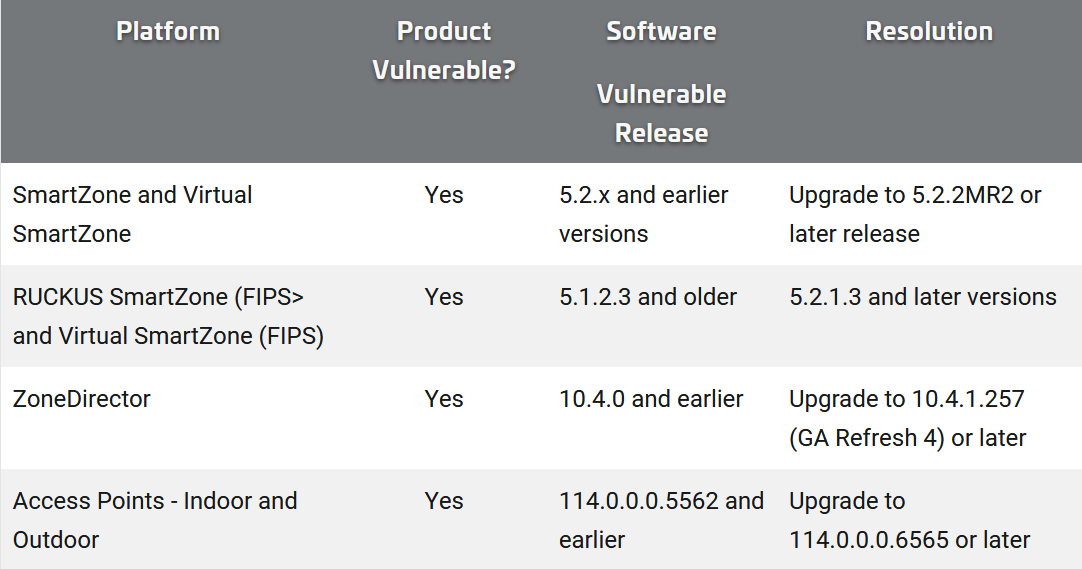
CISA added the RUCKUS Networks vulnerability to its “known exploited catalogue” on June 29. Among the affected products is RUCKUS ZoneDirector: software that is used to centralise “authentication and authorization decisions” for any Access Points (AP) across a given WLAN.
The vulnerability, allocated CVE-2023-25717, has a critical CVSS rating of 9.8. As an unauthenticated HTTP GET Request it is exploitable remotely, with no need for any user interaction, with a few very simple lines of code. (All it takes is a crafted URL. i.e. you can attack products via a web browser and then execute commands on the device, with no credentials needed.)
Among the 58 RUCKUS products affected by the vulnerability are routers and enterprise-level Wi-Fi access points designed to power WLAN applications for large service providers and public venues, stadiums, smart cities, “metro Wi-Fi” and others designed for small businesses.
The vulnerability was found by Ken Pyle, Partner at CYBIR, an incident response and digital forensics company. Pyle, who is also a professor at Philadelphia’s Chestnut Hill College, first reported it to RUCKUS Networks in early December 2022 and says the company did not register a CVE for the vulnerability saying simply “unfortunately we don’t have a CVE for this issue” or publish an advisory for customers until the day after he – frustrated at its response – posted exploit code on the bug on February 7.
He told The Stack: “Critical infrastructure, particularly network infrastructure, is rarely updated, carries a tremendous amount of tech debt, and is rarely examined for a variety of reasons. This [vulnerability affects] network infrastructure device[s] with wireless access.
“It's an open door into your network and backbone.”