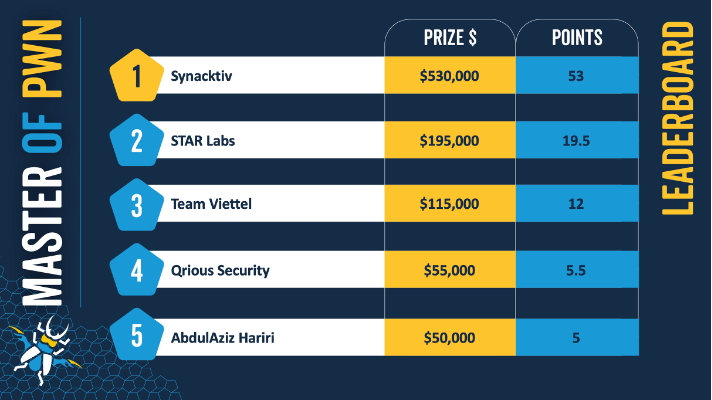
Hackers from French offensive security business Synacktiv have won the hotly contested “Master of Pwn” title by winning the annual Pwn 2 Own hacking competition – taking home $530,000, and a Tesla Model 3 after successfully demonstrating two hacks of the Tesla, along with breaches of Windows 11 and Oracle VirtualBox.
The event in Vancouver ran from March 22-24. It is led by Trend Micro's bug bounty arm the Zero Day Initiative (ZDI) – which reports vulnerabilities to vendors before they are demonstrated at the competitive event.
Prizes worth over $1 million were awarded across the following categories:
- Virtualization
- Web Browsers
- Enterprise Applications
- Servers
- Local Escalation of Privilege
- Enterprise Communications
- Automotive
Synacktiv’s Eloi Benoist-Vanderbeken, David Berard, Vincent Dehors, Tanguy Dubroca, Thomas Bouzerar, and Thomas Imbert’s two compromises of the Tesla (one taking just two minutes to demonstrate) included a “time-of-check-to-time-of-use (TOCTTOU)” attack on Tesla’s Gateway energy management system, along with a different attack that exploited a heap overflow vulnerability and an out-of-bounds write error in a Bluetooth chipset to break into Tesla’s infotainment system and, from there, gain root access to other subsystems.
They also hacked a fully patched Windows 11 desktop and demonstrated a chained attack against Oracle’s VirtualBox hypervisor with a host escalation of privileges, as well as a privilege escalation on Ubuntu Desktop.
Singapore's STAR Labs took second place, Vietnam's Team Viettel third place, a team called Qrious Secure took the fourth spot and Abdul-Aziz Hariri of Saudi Arabia' security firm Haboob took the fifth spot (among other successes, he took less than 15 seconds to demonstrate the successful exploit of Adobe Reader on macOS.)
Pwn 2 Own has now been running for 15 years, during which time offensive security research has become increasingly mainstream -- although no shortage of well known companies still neither have bug bounty programmes nor other vulnerability disclosure mechanisms; frustratingly for white hat hackers who have identified a vulnerability and want to responsibly disclose it before less benevolent actors find and exploit it.
On the other side of that coin are companies who do accept disclosures -- and have to triage an immense amount of them, many of them low-level outputs from fuzzing tools. The Apache Software Foundation, for example, which oversees 320 open source projects, received over 22,600 emails to its security email address in 2022 that had to be triaged by a team of volunteers supported by just one paid administrator. After spam filtering and thread grouping there were 1402 non-spam threads, but each had to reviewed to avoid missing real issues.
Department of Justice has vowed not to pursue "good faith" hackers
In May 2022 the US Department of Justice said that that it will no longer pursue hackers who breach networks or computers in “good faith”, saying: “Good faith security research means accessing a computer solely for purposes of good-faith testing, investigation, and/or correction of a security flaw or vulnerability, where such activity is carried out in a manner designed to avoid any harm to individuals or the public, and where the information derived from the activity is used primarily to promote the security or safety of the class of devices, machines, or online services to which the accessed computer belongs, or those who use such… online services.”
The announcement came amid revision of DOJ policy around how it will charge apparent breaches of the Computer Fraud and Abuse Act (CFAA); 1986 legislation that multiple courts of appeals have used to hold hackers civilly or criminally liable for accessing or probing a system for vulnerabilities without permission.
As Orin Kerr, Professor of Law at Berkeley and a cybersecurity specialist noted at the time: “It’s just a policy, not a law, so it’s just something to guide prosecutorial discretion and doesn’t create any rights in court…” but the DoJ appeared minded to uphold the policy firmly, noting that “all federal prosecutors who wish to charge cases under the Computer Fraud and Abuse Act are required to follow the new policy, and to consult with CCIPS [the department’s Criminal – Computer Crime and Intellectual Property Section] before bringing any charges."
The department added: "Prosecutors must [also] inform the Deputy Attorney General (DAG), and in some cases receive approval from the DAG, before charging a CFAA case if CCIPS recommends against it.”









