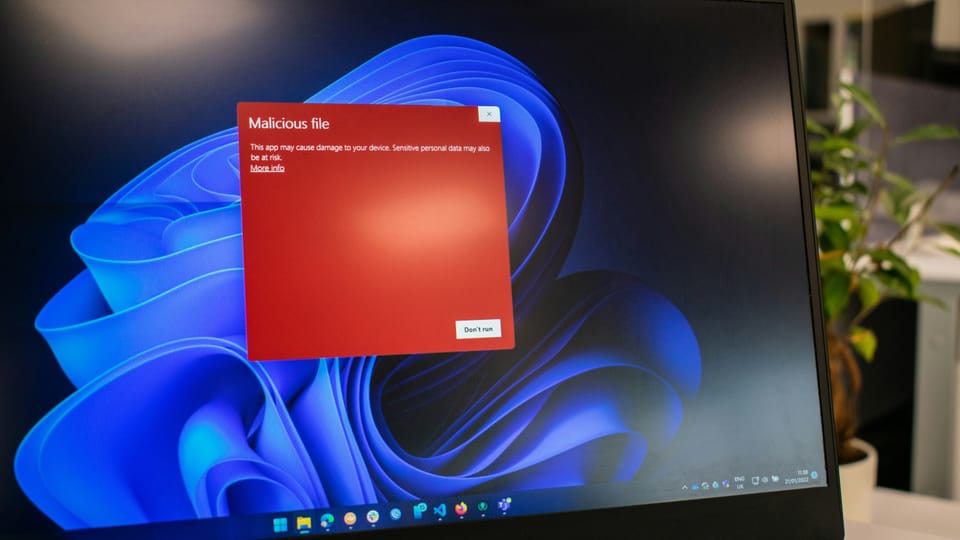
malware
Security
|
Jan 16, 2026
There looks to be a large group working on the project who have “big, big dreams, big goals, and they are iterating very fast,
CISA
|
Aug 01, 2025

"Users can define a series of modular steps—such as static file analysis, dynamic sandboxing, hash verification, unpacking, or signature detection"