Updated 16:58 with further threat actor claims.
Zscaler says an “isolated test environment on a single server” was publicly exposed to the internet – downplaying an alleged security incident and saying the exposed infrastructure had “no connectivity to Zscaler’s environments.”
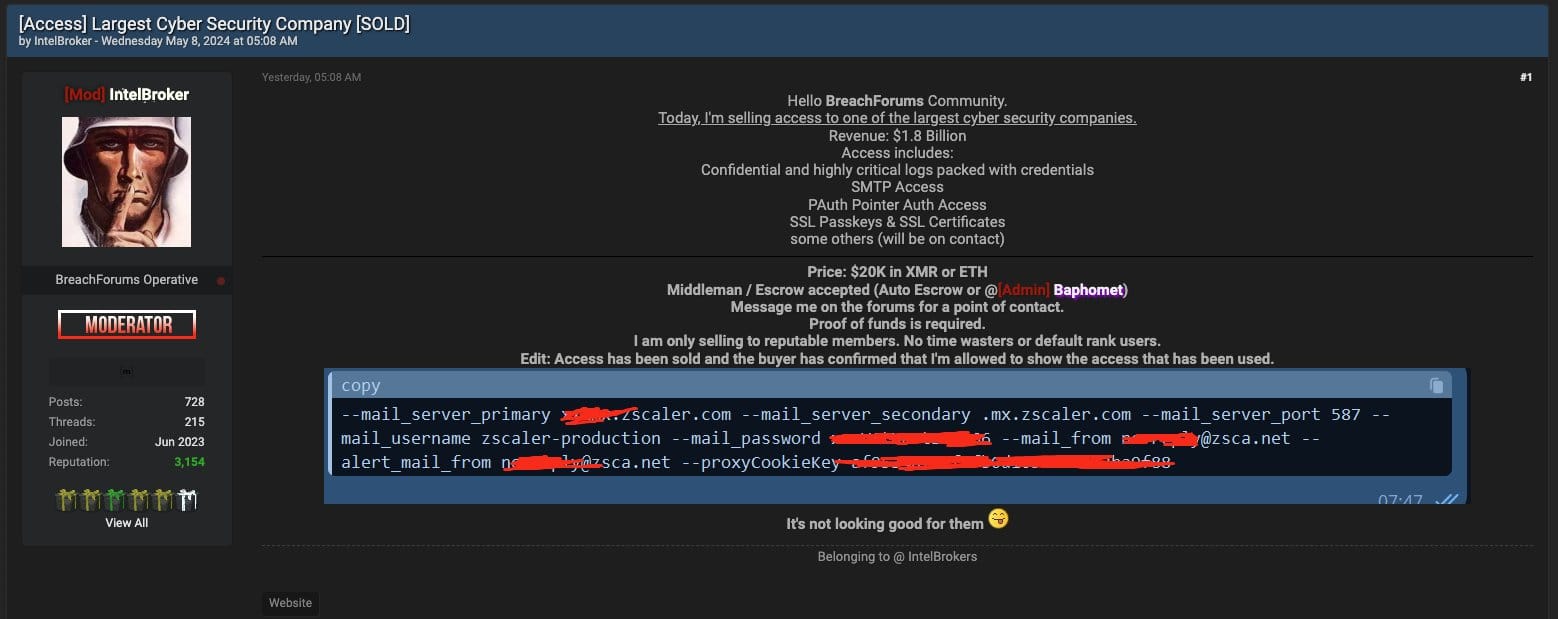
The comment comes after a threat actor claimed to have gained access to "confidential and highly critical logs packed with credentials.”
Later Thursday they rejected Zscaler's initial response, saying they had access to more than a test environment belonging to the company and had successfully sold it for $20,000 – including mail server access and SSL certs.
Zscaler provides "zero trust network access" via a cloud-native platform under a "SASE" model. It did not immediately comment on whether any credentials had been exposed via the exposed test environment.
The cybersecurity company’s thousands of customers include major government agencies and it is on track to earn $2.1 billion in 2024. Zscaler said in a short update that it “can confirm there is no impact or compromise to its customer, production and corporate environments.”
The Big Interview: Cato Networks CSO Yishay Yovel
A series of swift if initially detail-thin updates from the Nasdaq-listed firm came after a threat actor known as “Intel Broker” started selling alleged access to a “large cybersecurity company” for $20,000 in cryptocurrency this week – claiming that they had gained access to “confidential and highly critical logs packed with credentials” including alleged “SMTP Access - PAuth Pointer Auth Access - SSL Passkeys & SSL Certificates.”
Zscaler has been quick to respond, with updates coming regularly from the company after the claims first emerged.
Its latest update, posted shortly before 7am UK time today (May 9) said it “continues to investigate and reiterates there is no impact or compromise to our customer, production and corporate environments. During the afternoon of May 8, we engaged a reputable incident response firm that initiated an independent investigation. We continue to monitor the situation and will provide additional updates through the completion of the investigation.”
Zscaler breach: A sigh of relief?
There are grounds for cynicism on both the Zscaler breach claims and the company’s response: On the one hand, access brokers are incentivised to hype the scale of their access to ramp up market interest in their firesale.
Cybersecurity and other software companies meanwhile have been abundantly guilty in the recent past of underplaying the extent of a breach.
Okta for example in late 2023 belatedly admitted that a data breach had affected 100%, not 1% of customers. Microsoft in January 2024 went from talking about the Russian breach of “a very small percentage of Microsoft corporate email accounts” to shortly afterwards admitting access to source code repositories and internal systems that was used to hit customers.
See also: The Big Interview with JPMorgan Chase's Global CISO
A July 2023 Microsoft incident meanwhile was followed by a September 6, 2023 post-mortem that authorities this year described as misleading.
Redmond took six months to update the post-mortem after coming under pressure from the Cyber Security Review Board which said it was “troubled that Microsoft neglected to publicly correct [a] known error for many months” – referring to Microsoft’s false suggestion that it had conclusively identified how a cryptographic signing key was stolen from it.
“The loss of a signing key is a serious problem, but the loss of a signing key through unknown means is far more significant because it means that the victim company does not know how its systems were infiltrated and whether the relevant vulnerabilities have been closed off” the CSRB said.
“Left with the mistaken impression that Microsoft has conclusively identified the root cause of this incident, Microsoft’s customers did not have essential facts needed to make their own risk assessments about the security of Microsoft cloud environments in the wake of this intrusion. Microsoft told the Board early in this review that it believed that the errors in the blog were “not material.” The Board disagrees,” it noted.
Errors by certain companies should not be enough to tar an entire sector with the same brush, but there is a distinct industry trend of playing down breaches early on. Zscaler customers will no doubt be continuing to watch closely. Thus far the company has not publicly made any security recommendations to its customers like rotating credentials.
Stay tuned.








