If you work outside the US Federal Government and are even tangentially in cybersecurity, you are likely aware of the Cybersecurity and Infrastructure Security Agency (CISA), which was founded in 2018 under the Department of Homeland Security; if just from its vulnerability alerts and useful – if not always blisteringly quick – “known exploited” catalogue.
The agency’s increasingly muscular approach to working with other agencies inside the federal government to improve their security posture is less well known, as is its $7 billion “Continuous Diagnostics and Mitigation” (CDM) project – a centralised asset discovery and vulnerability management programme that has a growing pan-agency reach.
(It now touches close to three-million endpoints across some 92 agencies; working across what are historically fiercely independent organisations who do not want their networks interfered with in any way.)
The Government Accountability Office (GAO) warned earlier this year however that the CISA CDM programme has “had issues demonstrating that key performance parameters are met because the CDM program cannot test its tools on other agencies’ networks without agency permission” and that “as of September 2022, the program did not have permission from any agency to conduct operational testing.”
An earlier 2020 report from GAO had also emphasised that agencies were not managing to meet CISA’s hardware management demands because “contractors, who install and troubleshoot the tools, [were] not always providing unique identifying information. Accordingly, CDM tools did not provide an accurate count of the hardware on their networks.”
(You can’t protect what you don’t know you have…)
See also: US agencies tells users to deploy 'independent encryption' across satellite comms. It's not that easy
For a federal programme of this scale and given CISA’s broader positive reputation, the reports raised some red flags with The Stack.
We arranged a conversation with CDM programme manager Matt House, who described GAO's criticisms as born out of the fact that GAO was working with very specific definitions created for parent agency the DHS and predicated on the fact that traditionally DHS had built tools for itself.
CISA's CDM had, he said, pioneered the centralised oversight of pan-agency vulnerability management and asset discovery, as well as delivered real procurement efficiency: the bargaining power and economies of scale created by buying security toolings for a wide array of federal agencies combined helped deliver when negotiating with cybersecurity vendors.
The Q&A of our conversation below has been edited for brevity.

Let’s recap: What is CISA's CDM?
We're still true to our roots in terms of what our initial objectives were, which is to help strengthen the cyber defences of what we call the ‘Federal Civilian Executive’ – the federal civilian agencies within the US government. [Ed: Agencies that fall under CISA’s extensive authorities include the Departments of Commerce, Energy, Homeland Security; Justice, Labor, State, as well as organisations like the Peace Corps, SEC and many others.]
Initially, our focus was on helping the agencies level-up, with respect to being able to identify cyber risks and take effective action on them.
“Our goal was to get all of the agencies – whether they are a very large agency with 100k+ endpoints and tens of thousands of employees, all the way to the small ones that are in the order of 12 employees, each of which wear multiple hats – up to that same level of parity; and do so in a way that we're all speaking the same language and using the same visualisations, so when I say something is "urgent", you understand what my definition is.
“We've grown wildly in terms of what we're doing with agencies...

What’s the main focus?
“We still look at the world roughly in terms of four sets of capability families. Our core is asset management: What's on the network: devices, hardware, software; what are their configuration settings; what are the vulnerabilities associated with those devices.
We're now rounding out our work on traditional endpoints – typical desktops, laptops, server endpoints – and shifting into new asset classes. Mobile devices are the hot and heavy class for us today, as are cloud assets.
“We're looking to apply equivalent capabilities to our second family of capabilities, identity and access management (IAM). So understanding how agencies manage credentials, privileged access, identity lifecycle, are much a focus for us in terms of active work we're doing with agencies.
The third capability set is network security management. We've expended a lot of effort in this area over the past two and a half years or so, as we put our EDR initiative [in place] that's mandated by the White House through Executive Order 14028. [The aim is to provide] phenomenally precise detection, reconnaissance and response capabilities, throughout the better part of 3.5 million endpoints.
Then our fourth capability area is data protection.
“That’s the one we've worked the least thus far… it still involves what we defined 10 years ago, which is understanding what data is on the network, whether that sensitive data is protected at the right levels…”
How do you work with private partners on this? Is there much custom in-house building happening? And what do these capabilities actually look like at the coalface for you and for partnering agencies?
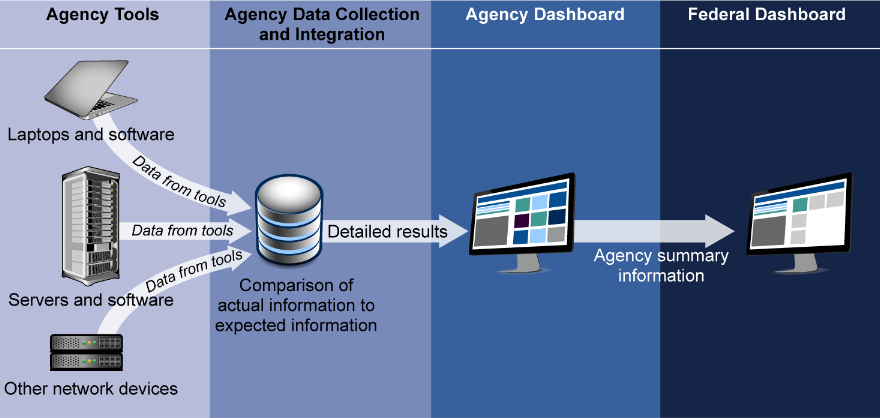
Whatever flavour of of cheese we're putting through the machine, we follow a logical four-tiered structure.
Layer A is where we work with the agencies to deploy the tool [and start generating raw data]. Everything we're doing in Layer A with agencies is based on COTS products. We don't do any custom in-house development of those capabilities. [In terms of how] we partner with private industry, 11 times out of 10, they've looked at the problem much better than the government would, at a timescale that is far more efficient.
“We don't mandate in Layer A what tools an agency has to use [as long as they are] functionally equivalent and meet a set of requirements.
In Layer B, we collect the data from from the raw sensors, and we do a lot of data management; we pull out the data attributes that we're interested in, we normalise that, and we turn it into a coherent data set so that what is reported by Agency 1, is coherent with what's recorded at Agency 2.
“That is a combination of COTS products and some custom work.
“Layer C is the agency dashboard. All of our agency operator partners use the agency dashboard, that's their lens into everything we're doing. We within the programme develop that, we treat it like a product, and then we hand it out to all of the agencies.
“Then layer D is the federal dashboard. That's the dashboard that’s the ‘one ring that rules them all’, if you will. It lives up with us and it has purview to look across all agency dashboard instances… we have some more customised and unique visualisations for macro-level use cases.

What’s the reach now across agencies?
Depending on the week our universe is about 100 agencies. We’re at about 92 that have the dashboard deployed and are working with us.
Talk to us about this GAO report: It flagged an additional $509 million expected spend for the incorporation of “EDR into network security management”. Why was this not incorporated into original budgets?
This was a new requirement. [In May 2021] The White House issued an executive order that gave very specific requirements about agencies having to deploy EDR. We at CDM were tapped to run the initiative for the federal government. So that's why… what we expended was so high because it's across three million endpoints or so that are in our scope.
What we do with those agencies is on a case-by-case basis with each agency. They select the COTS tool if they don't already have one, we'll work with them to kind of do that analysis of what's the best fit in a collaborative fashion.

Going back to this challenge of contractors putting machines on a network but not sharing the information you need to log them properly. Is that still an issue?
[On the contractor issue] I think it's an area where we are making a lot of progress. And I think this is a good example of where to compare and contrast today's CDM and today’s CISA versus where we were a few years ago: We have much greater interoperability as a programme with other facets of what CISA is doing. So we have policy functions within CISA that issue guidance and directives to agencies to say ‘thou shalt do XYZ.’
We’re reaching a level of maturity within the CDM programme to ensure that the agency can now track [other departments’] progress… we've issued binding operational directives in the past two fiscal years that have really tried to tackle this problem in particular; dealing with things like vulnerability reporting and asset coverage. That was in large part driven [by a need to reduce] gaps in coverage that are spoken to in that GAO report.
Most, if not all of our largest, most federated complex agencies are getting to a level of coverage and visibility of their own devices and assets that gets us to pretty close to a level where we can shift our focus on to other areas that are more urgently in need. But this will require constant maintenance and monitoring. Right? It's not like a milestone you hit once and then you let off the gas. But since GAO collected its data, we have made tremendous progress.

Both federal procurement and cultural change internally can be challenges for this kind of programme. How are you tackling them?
You nailed it. It is definitely the change management that is the most complicated...
In terms of procurement, what we do with CDM, compared to 10 years ago, is unprecedented. There's no other agency trying to do the same thing across 100 agencies in roughly the same manner: There wasn’t [a cybersecurity] agency, like OMB that owns all the budgeting functions and is top of the anthill.
We had plenty of inertia to overcome in terms of Federal Acquisition mechanisms. But we have gotten very smart on how to do business with agencies and build flexibility into our contracting vehicles.
See also: Critical controller bug could trigger traffic chaos: Software vendor ignores CISA outreach
We we took an approach early on to try and divide and conquer; to break things up into different capability sets and prioritise those.
“We broke things up in terms of having teams that were dedicated to certain agencies, and contracts that were dedicated to certain agencies. That gave us some flexibility, so that we didn't have to try and do the same thing to everybody all at once. So our contracting structure and our procurement models are unique. Compared to what you'll see in other governments constructs. We will purchase the COTS tools for the agencies; we'll fund the effort to implement them; and we'll cover up to two years worth of licencing and effort with the goal of ‘let's get it operational.’ During that two year period of time while we're doing that work, the agency is learning how to use the tool and maintain it. They're programming it into their own budgets. So we start to have some sort of coordination in terms of budget, planning and execution. And then when we make that handoff, it's not tossing something over the fence, it's more of a deliberate handshake that we that we make with the agency.
And our buying power is magnified: When we say we're buying this on behalf of all these agencies, vendors listen differently.

Let’s go back to that change management element. How do you handle that?
We have roughly 100 different ways that we get that done. It is all still 100% Relationship Management, knowing each agency has its own unique constraints, working within those constraints, and working collaboratively to thread the needle between driving standardised enterprise approach cyber defence implementation, and letting agencies be self-determining and what they need to manage. We don't want to manage their networks; we don't want to get in the way of them managing their daily business, those kinds of things…”
On networks… Per GAO, why won't any agency that you conduct operational testing on their networks? Seems like a significant issue?
When we talk about operational testing as a proper noun, that has very, very specific definitions within the context of the Department of Homeland Security, which is our parent agency. Those requirements were born out of the expectation that when DHS is building a system or a capability, it's for their own use; they're building capabilities to secure ports and they operate those capabilities themselves; they're all maintained and operated by the same entity that designs and builds.
That’s not the case here, our goal is to get the kids out of the house after college: Get these capabilities operational hand them off to the agencies.
It’s not that agencies don't want to work for us. It's that the requirements [alluded to in the GAO report] are a DHS-driven set of requirements and there’s a lot more work we have to do – related to change management and how test responsibly without stepping on agencies’ abilities to run their networks and do daily business – that we just have to negotiate.
Nobody has said “no, they just say, “what's operational testing?” And then we've got to work through those details. We are doing operational testing and agencies are part of that process today. It just takes time.
Closing words?
In particular, over the last few years with the EDR work that we've done, we have newer authorities granted to us that allow us to do a lot more in depth inspection of agency data. That’s not to beat up agencies but to work with them more efficiently. We have this macro-level view, and we can look across and we can see ‘okay, agency over here is having an issue.’
“And we can work with them very quickly and off the same sheet of music, isolate, diagnose and remediate. And then we can go and pivot – we're the only ones who can do this – pivot over to another agency, or all these other agencies and say, do we see the same thing anywhere else?”
So you don’t have 100 agencies ground-up trying to solve the same problem in isolation. We are now this coordinated response mechanism.
What I'm most excited about, especially over the next 12 months, is continuing to build out the technical capabilities there. We were working on what does coordination mean? How do we establish standard operating procedures? How do we, you know, really wring as much out of that investment as possible, so that we are doing really effective threat hunting. We want to be in the mode where CDM’s tooling and operational visibility, is the frontline defence for all agencies and sets the standard.”








