Updated 16:45 BST, March 13, with comment from CISA.
America’s primary cybersecurity agency, CISA, lacks the skilled staff and capabilities to tackle the nation’s growing Operational Technology (OT) security issues, said an influential congressional watchdog – even as critical national infrastructure faces increased attacks from hackers.
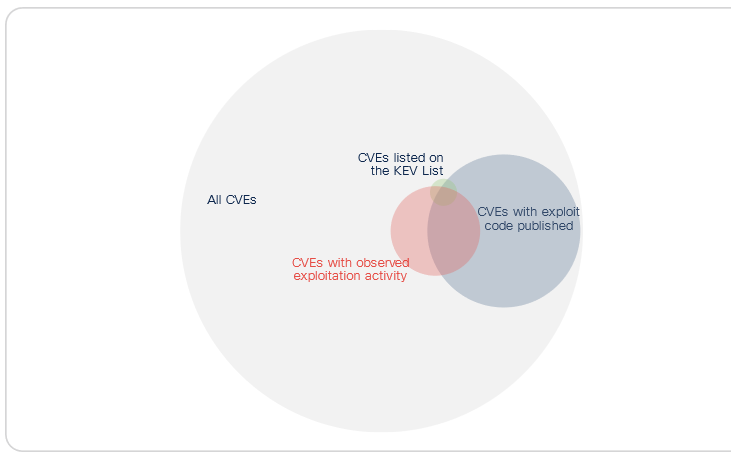
The warning, in a Government Accountability Office (GAO) report published on March 7, came as OT security specialist Forescout claimed that only 35% of exploited vulnerabilities in the OT sector appeared in CISA’s “Known Exploited” catalogue (“KEV”) – suggesting a huge blindspot.
(Federal law designates CISA as the lead agency for helping critical national infrastructure owners to address cybersecurity risks to OT and between 2019 – 2023 it provided 13 OT products and services to critical infrastructure owners and operators; it has since dropped three of them.)
Strikingly GAO's report reveals that CISA has just two federal staff and five contractor staff working on its OT-specific threat hunting and/or incident response services – despite the Department of Homeland Security stating that "cybersecurity threats to critical infrastructure are one of the most significant strategic risks for the United States, threatening our national security, economic prosperity, and public health and safety."
CISA'sExecutive Assistant Director for Cybersecurity, Eric Goldstein told The Stack: “Hiring cybersecurity experts, particularly those with experience in Industrial Control Systems (ICS), is a universally acknowledged challenge for every organization and is a strategic focus for CISA. We’ve continued our efforts to deepen and expand our operational technology (OT) and ICS workforce, including bringing on team members with deep ICS expertise across our organization."
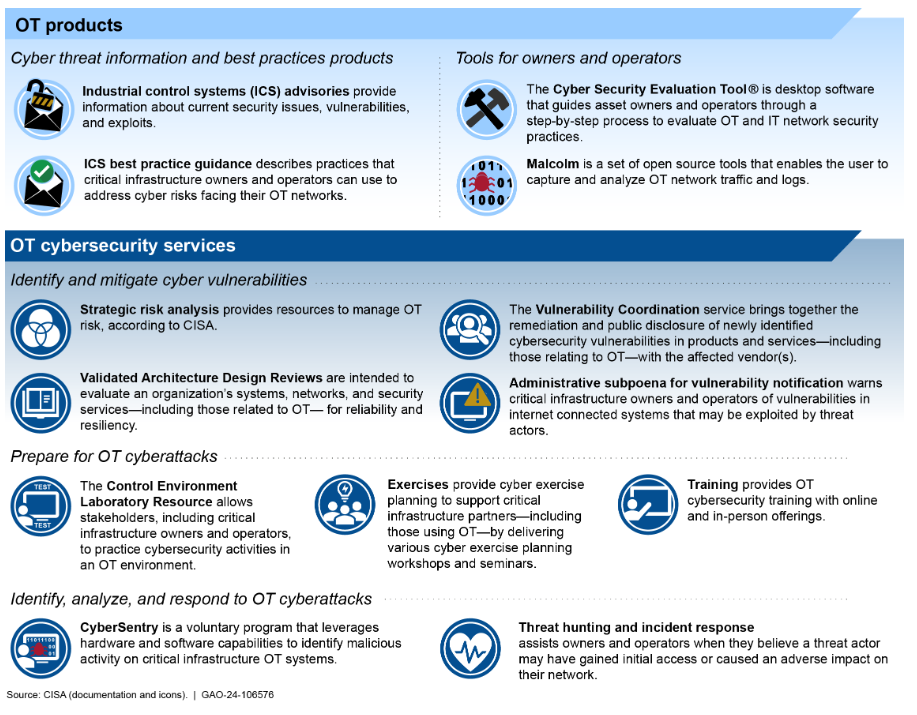
Seven of the 13 non-federal entities who deal with OT aired grievances of negative experiences when using CISA’s products and services. Complaints included issues around CISA’s validated architecture design reviews and vulnerability coordination – both of which face length delays.
As the GAO put it: “CISA does not have enough staff to provide the reviews to all that requested it. Demand for this service increased after the Transportation Security Administration (TSA) required that certain pipeline owners and operators conduct architecture design reviews of their OT systems, and stated that validated architecture design reviews conducted by CISA would satisfy this requirement…”
(A ransomware attack on the largest pipeline for transporting refined petroleum products in the United States in 2021 – Colonial Pipeline – shut down its operations for approximately five days, causing shortages of petrol, diesel, and jet fuel. Prior to that attack, federal authorities had taken a highly “hands-off” approach to cybersecurity; the TSA had suggested voluntary best practices standards to pipeline companies, but even physical security assessments had no enforcement capability.)
One entity told the Government Accountability Office (GAO) that vulnerabilities reported through CISA’s process often take more than a year between the initial report of a vulnerability and public disclosure. (CISA rejected that characterisation, saying it has a 45-day disclosure policy and if a vendor or researcher stops responding it “will work with the remaining stakeholders to agree on an appropriate timeline…”)
Daniel dos Santos, Head of Security Research at OT security firm Forescout, agreed that OT vulnerabilities are slipping the net. Pressed for examples by The Stack, he said: “Some examples of CVEs we see exploited and did not make it to CISA KEV include CVE-2023-26801 affecting LB-LINK routers, CVE-2022-37061 affecting Teledyne FLIR AX8 cameras and CVE-2022-25075 affecting Totolink routers, as well as vulnerabilities without a CVE ID such as EDB-48225 affecting Netlink GPON routers.
He added: “These are probably overlooked because of CISA's criteria for inclusion in their list (assigned CVE, active exploitation and clear remediation guidance,) which would exclude the ones without a CVE ID and those that do not match their “active exploitation” definition, although it is unclear what they mean by that and it is a known fact that CISA’s list has limited coverage by design…”
“CISA is facing a challenging task,” dos Santos added. “As the number of connected devices grows, coupled with the increase in number and sophistication of threat actors, it becomes even more challenging to prevent and respond to cyberattacks.”
Staffing appears to be a clear blocker for CISA. The GAO said that since the agency began comprehensively tracking OT infrastructure reviews in 2019, it has only been able to fulfil 125 of the 572-OT related requests for these reviews as of May 2023 and only has four federal employees and five contractor staff on its threat hunting and incident response service.
These thin staff numbers, according to the report, are also hurting interaction and collaboration with federal entities.
Moving forward, GAO recommends that CISA perform effective workforce planning for OT staff and that it measure customer service for its OT products and services more robustly.
The US's agency fiefdoms also remain a challenge. CISA needs to work closely with Sector Risk Management Agencies (SRMA) - a federal departments or agencies, designated by law or presidential directive, with responsibility for providing institutional knowledge and specialized expertise for a particular sector. But GAO found that "CISA officials were not aware of any agency policies for developing agreements with SRMAs regarding collaboration to mitigate cyber OT risks."
The thresholds for where an SRMA needs additional assistance is "set by
CISA’s Stakeholder Engagement Division. However, CISA did not
provide documentation of these thresholds" GAO found, adding "Until CISA develops and implements a policy on agreements with SRMAs regarding
collaboration to mitigate cyber OT risks, CISA may continue to
experience challenges in interagency collaboration."
CISA's Goldstein added to The Stack: "We continue to align our organization to most effectively support our partners in managing ICS cybersecurity risks, such as by establishing a new cyber-physical forensics team and hiring a senior leader to guide our critical infrastructure threat detection strategy.
"More broadly, we continue to refine our approaches to recruit and hire ICS cybersecurity personnel, including by updating technical competency requirements and assessments for ICS cybersecurity positions and implementing a sustained hiring strategy for ICS roles.”








