Dell Wyse ThinOS 8.6 and prior versions contain a brace of CVSS 10 critical vulnerabilities, that could give a remote, unauthenticated attacker the ability to -- in Dell's own words -- "manipulate the configuration of any target specific station" and "gain access to sensitive information on the local network, leading to the potential compromise of impacted thin clients."
Uncomfortably for the company, Dell describes the products -- small computers optimised to perform desktop connections to remote and more resourceful hardware -- as "the most secure thin client operating system delivering a rich user experience with the latest high-performance desktop virtualization protocols and a broad array of connectivity options".
The bugs (tracked as CVE-2020-29491 and CVE-2020-29492) were spotted by healthcare security specialist CyberMDX Research, which said it spotted the Dell Wyse Thin clients using the unencrypted, generally insecure File Transfer Protocol (FTP) with no authentication. (Insert grimace here).
It estimates that over 6,000 organszations are using Dell Wyse thin clients inside their network in the US alone; many of them healthcare providers.
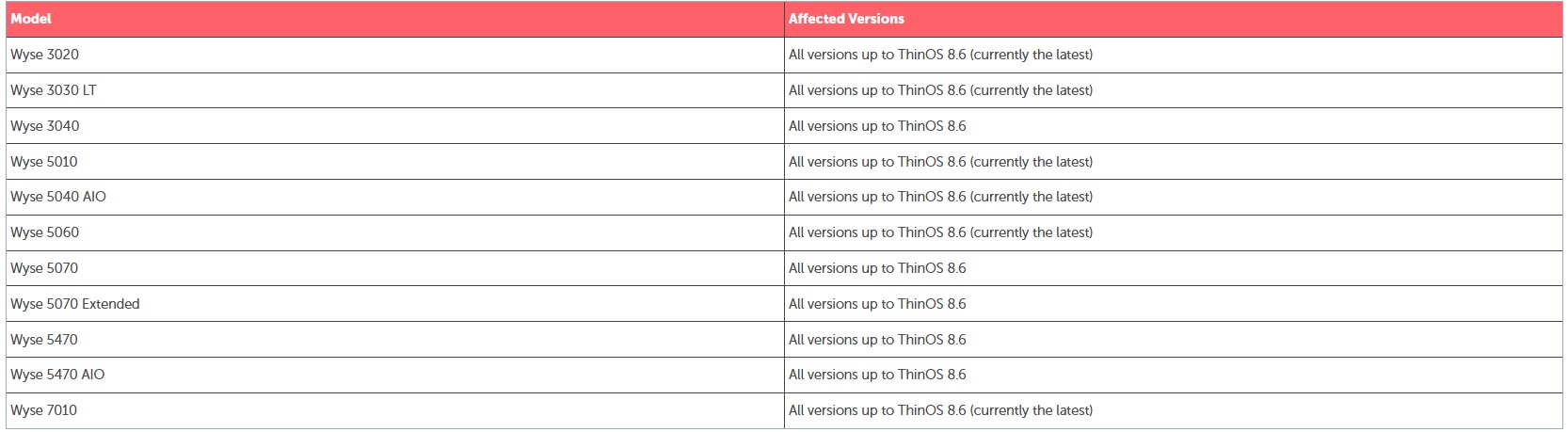
Dell Wyse ThinOS CVEs
"FTP is used by Wyse thin clients to pull their configurations from a local server. The team further discovered that the server where the configurations are stored permits "read and write" access to its configuration files, enabling anyone within the network to read and alter them using FTP" CyberMDX said in its December 21 advisory.
"One of the main issues is that security is often overlooked during the design phase of these devices," added Elad Luz, Head of Research at CyberMDX. "The default installation of the server for the Thin Client devices FTP server is configured to have no credentials ('anonymous' user) and this enables anyone on the network to access the FTP server and modify the INI file holding configuration settings for the thin client devices.
He added: "Even if credentials are enforced they would still have to be shared across the entire Thin Client fleet, which would enable any Thin Client to access and/or modify the configuration of all other Thin Clients within the network which is still an issue."
Dell noted that it "advises creating an FTP server using Microsoft IIS (no specific guidance), then giving access to firmware, packages, and INI files accessible through the FTP server. The FTP is configured to have no credentials (“anonymous” user). While the firmware and package files found on the FTP server are signed, the INI files used for configuration are not. Additionally, there is a specific INI file on the FTP server that should be writable for the connecting clients (this is by design). Since there are no credentials, essentially anyone on the network can access the FTP server and modify that INI file holding configuration for the thin client devices.
The company added: "When a Dell Wyse device connects to the FTP server it searches for an INI file in the form of “{username}.ini” where {username} is replaced with the username used by the terminal. If this INI file exists, it loads the configuration from it. This file... can be created and manipulated by an attacker to control the configuration received by a specific user."









