Microsoft has identified a new North Korean threat group that it calls Moonstone Fleet. The group is delivering custom ransomware, using a combination of hands-on-keyboard tactics, social engineering and even a “tank game” it developed to breach organisations with a financial motive.
In December the North Korea-affiliated group breached a defense technology company to steal credentials and intellectual property. In April 2024, it then ransomed the same company using its custom malware, FakePenny. That same month it breached a company that makes drone technology, said Microsoft Threat Intelligence, adding: “In May 2024, the threat actor compromised a company that makes aircraft parts…”
Moonstone Fleet has been seen delivering a trojanized version of PuTTY, an open-source terminal emulator, via apps like LinkedIn and Telegram as well as developer freelancing platforms said Redmond. It has taken approaches like setting up fake companies to send .zip files invoking a malicious npm package under the guise of a technical skills assessment and setting up fake companies impersonating software development and IT services and used them to reach out to potential targets with offers.
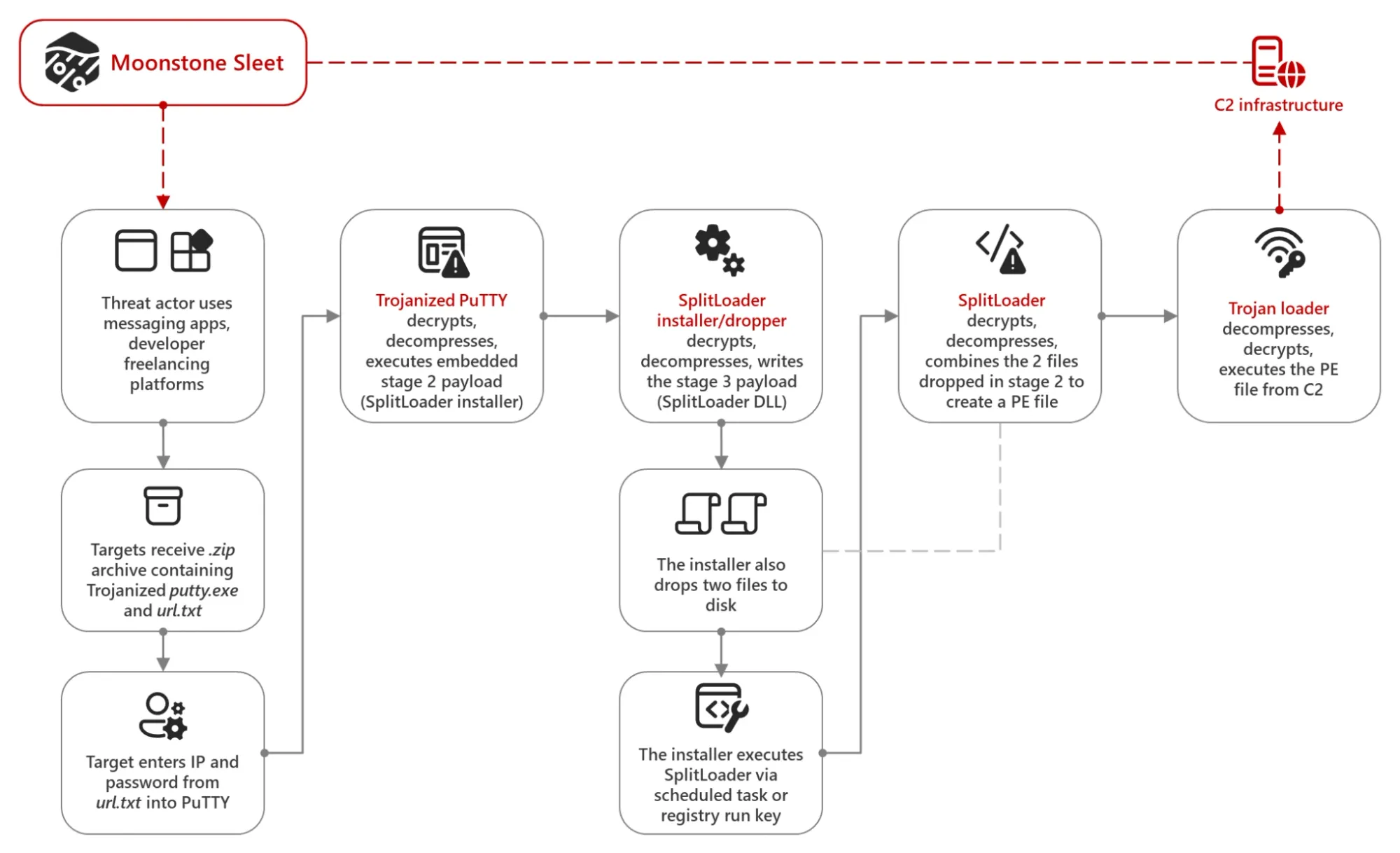
It even set up a fake “tank game” that delivered malware called “DeTankWar (also called DeFiTankWar, DeTankZone, or TankWarsZone).”
(Of Redmond's nine recommendations to defend against Moonstone Sleet attacks, seven of them involve suggesting users buy or deploy Microsoft cybersecurity products, although it also shared some IOCs and malicious domains associated with the new threat group.)
Microsoft’s May 28 post comes two weeks after the US Department of Justice unsealed charges against several people over alleged “schemes to place overseas information technology (IT) workers—posing as U.S. citizens and residents—in remote positions at U.S. companies.”
“The overseas IT workers gained employment at U.S. companies, including at a top-five major television network, a Silicon Valley technology company, an aerospace manufacturer, an American car manufacturer, a luxury retail store, and a U.S.-hallmark media and entertainment company, all of which were Fortune 500 companies. Some of these companies were purposely targeted by a group of DPRK IT workers, who maintained postings for companies at which they wanted to insert IT workers,” the DoJ said on May 16.
Its charges revealed that alleged co-conspirators ran U.S. based “laptop farms” that allowed overseas IT workers to remotely access those laptops through various software applications; earlier guidance by the State Department and South Korean cybersecurity authorities called for companies to “Prevent remote desktop protocol from being used on all company devices and prohibit using remote desktop applications for work” (good luck with that), to “Require freelancers to shut off commercial VPNs when accessing company networks” and to audit or at least request documentation of third-party staffing firms of their background check processes.








