Security

The attack has been claimed by the prolific LockBit group, which has hit numerous high-profile companies in recent months, often using unpatched Citrix Bleed vulnerabilities.

"Cozy Bear" gained unauthorized access to HPE’s cloud-based email environment

A 10-line exploit is now widely available. Unpatched instances *will* come under attack.

Over 26 billion records compromised in newly discovered trove of multiple breaches.
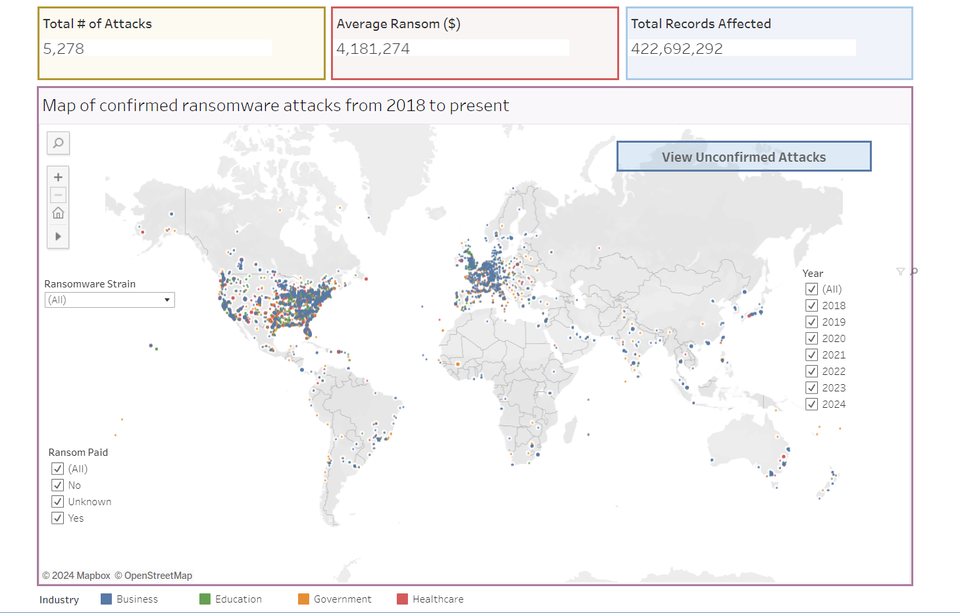
"Over 102.4 million records were breached via ransomware attacks on tech companies in 2023–a staggering 2,300 percent increase on 2022’s figure of 4.26 million. It’s also the highest number recorded across any industry since we began tracking confirmed ransomware attacks in 2018..."

A rewritten EU cyber resiliency act removes the biggest threats to open source but much standards work still to be done, says Linux Foundation Europe

"We will act immediately to apply our current security standards to Microsoft-owned legacy systems and internal business processes..."
There are no workarounds that remove the vulnerability, which allows unauthenticated remote command execution on vulnerable systems. A patch is available.
