Some 75,000 Cyber Essentials certificates have been issued since the launch of the security benchmark established by the NCSC, the agency said this week in its annual report. That means just 1.3% of the UK’s 5.6 million* private businesses have been awarded the respected cybersecurity certificate. So what does Cyber Essentials require? The certificate specifies requirements under five technical control schemes:
- Firewalls
- Secure configuration
- User access control
- Malware protection
- Security update management
These are provided to the certifying body via a verified self-assessment that costs just £300+VAT. Better yet, companies with a turnover under £20 million achieves self-assessed certification covering their whole organisation are entitled to free cyber insurance covering data breaches, ransomware and more (up to £25,000).
There's a host of certification bodies out there that can help you.
Cyber Essentials certification aims to give you “peace of mind that your defences will protect against the vast majority of common cyber attacks” as the NCSC puts it – it will also allow you to bid for central government contracts. What does Cyber Essentials require, specifically? The Stack took a closer look at the requirements – which were updated in April 2021 to reflect changes to wording around VPNs, BYOD, requirements around third-party account access and software firewalls (among a number of other changes detailed by partner IASME here.)
Although it aims to simply help organisations remove low hanging fruit that may draw attacks, as one CIO who works extensively with SMEs told The Stack this week “Things like Cyber Essentials can actually be quite hard to achieve in legacy environments where things have been allowed to get out of date; particularly in industries like manufacturing, where there's often legacy operational technology to worry about as well.”
What does Cyber Essentials require?
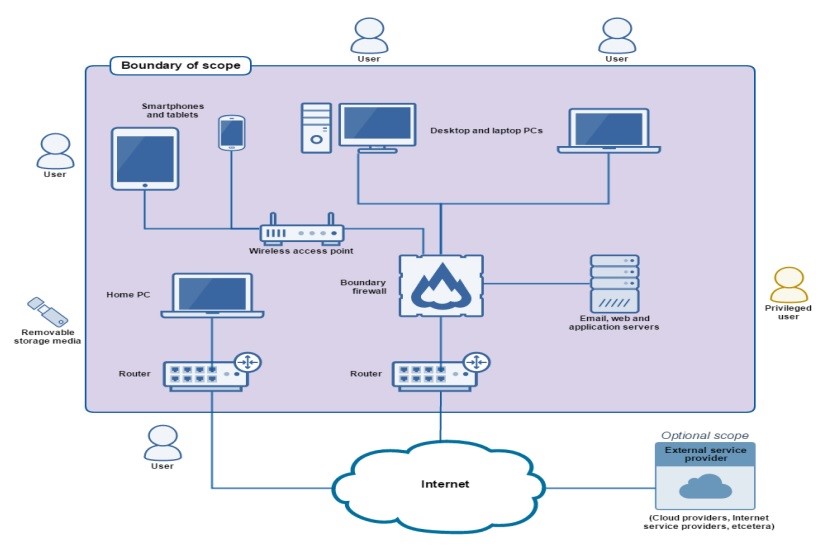
1: Firewalls
The firewall requirements apply to: boundary firewalls; desktops; laptops; routers; servers.
Every device that is in scope must be protected by a correctly configured firewall (or equivalent network device). Applicants wanting to meet the Cyber Essential requirements must routinely:
- change any default administrative password to an alternative that is difficult to guess
- (see Password-based authentication) — or disable remote administrative access entirely
- Prevent access to the administrative interface (used to manage firewall configuration) from the Internet, unless there is a clear and documented business need and the interface is protected by one of the following controls: 1) a second authentication factor; 2) an IP whitelist
- Block unauthenticated inbound connections by default
- Ensure inbound firewall rules are approved and documented by an authorised individual
- Remove or disable permissive firewall rules quickly, when they are no longer needed. Use a host-based firewall on devices which are used on untrusted networks, such as public Wi-Fi hotspots
2: Secure Configuration
The secure configuration requirements apply to: email, web, and application servers; desktop computers; laptop computers; tablets; mobile phones; firewalls; routers and aim to minimise inherent vulnerabilities.
It is designed to reduce the risk from default configurations, as well as brute force attacks.
Cyber Essentials requirements for this category are:
- Lock accounts after no more than 10 unsuccessful attempts
- Limit the number of guesses to no more than 10 guesses within 5 minutes*
- Set a minimum password length of at least 8 characters
- Not set a maximum password length
- Change passwords promptly when the Applicant knows or suspects they have been compromised
Applicants should also have a password policy that tells users:
- How to avoid choosing obvious passwords (like the name of a favourite pet)
- Not to choose common passwords — consider using a password blacklist
- Not to use the same password anywhere else, at work or at home
- Where and how they may record passwords to store and retrieve them securely
- If they may use password management software — if so, which software and how
- Which passwords they really must memorise and not record anywhere
3: User Access Control
The user access control Cyber Essential requirements apply to email, web and application servers; desktops, laptops, tablets; and mobile phones and are designed to reduce the risk of hackers accessing admin accounts.
The Applicant must be in control of its user accounts and the access privileges granted to each user account. It must also understand how user accounts authenticate and control the strength of that authentication. This means the Applicant must:
- Have a user account creation and approval process
- Authenticate users before granting access to applications or devices, using unique credentials
- Remove or disable user accounts when no longer required (i.e. when a user leaves the organisation or after a defined period of account inactivity)
- Implement two-factor authentication, where available
- Use administrative accounts to perform administrative activities only (no emailing, web browsing or other standard user activities that may expose administrative privileges to avoidable risks)
- Remove or disable special access privileges when a member of staff changes role, for example
4: Malware Protection
Cyber Essentials applicants need to implement a malware protection mechanism on all devices in scope (desktops, laptops, tablets, mobiles) and use at least one of the three mechanisms listed below:
Anti-virus software
- For AV software, keep it (and all associated malware signature files) up to date, with signature files updated at least daily. This may be achieved through automated updates, or with a centrally managed deployment.
- Configure this software to scan files automatically; including when downloaded and opened, and when they are accessed from a network folder; ditto for web pages – and “prevent connections to malicious websites on the Internet (by means of blacklisting, for example) — unless there is a clear, documented business need”
Application whitelisting
- Only allow approved applications, restricted by code signing, to execute on devices
- Actively approve such applications before deploying them to devices
- Maintain a current list of approved applications Users must not be able to install any application that is unsigned or has an invalid signature
Application sandboxing
All code of unknown origin must be run within a ‘sandbox’ that prevents access to other resources unless permission is explicitly granted by the user. This includes:
- Other sandboxed applications
- Data stores, such as those holding documents and photos
- Sensitive peripherals, such as the camera, microphone and GPS
- Local network access
5: Security Update Management
Applies to web, email and application servers; desktops, laptops; tablets; mobile phones; firewalls; routers.
The Applicant must keep all software up to date (and this is where it can get most problematic for SMEs running hardware on legacy boxes with complex and not always clearly understood dependencies.)
The NCSC says software must be:
- Licensed and supported
- Removed from devices when no longer supported
- Patched within 14 days of an update being released, where the patch fixes a vulnerability with a severity the product vendor describes as ‘critical’ or ‘high risk’
*Needless to say, not all of the UK's 5.6 million private businesses are large enough to want to consider the certificate. Many are sole traders. There are still hundreds of thousands, if not millions of SMEs for whom the low cost and sensible nature of the controls it requires mean it would be a great idea to get certificated.









