Some 15 million publicly exposed instances remain vulnerable to nearly 900 known exploitable vulnerabilities catalogued by the US’s Cybersecurity and Infrastructure Security Agency (CISA) over the last decade.
That’s according to analysis by security firm Rezilion based on analysis of Grey Noise and Shodan data – with Rezilion noting that more than a quarter of the known exploited vulnerabilities in CISA’s “KEV” catalogue are in the products of just three companies: Adobe, Google, and Microsoft, with the latter dominating.
The company said that more than 800,000 machines are still exposed to known exploited vulnerabilities that are over five years old. (If some of these are honeypots, credit to those running them for keeping them alive and pulling data in exploitation attempts so many long years after the vulnerabilities in question were revealed.)
Almost 200,000 exposed hosts remain vulnerable to CVE-2014-0160, aka Heartbleed, disclosed nine years ago. Some 14.5k and 4.9k machines remain exposed to widely reported 2021 bugs ProxyShell and ProxyLogon.
Using data from Greynoise, the researchers established that the Confluence bug CVE-2022-26134 was the most exploited, with over 800 exploitation attempts in the past month alone; that’s roughly one attempt every hour.
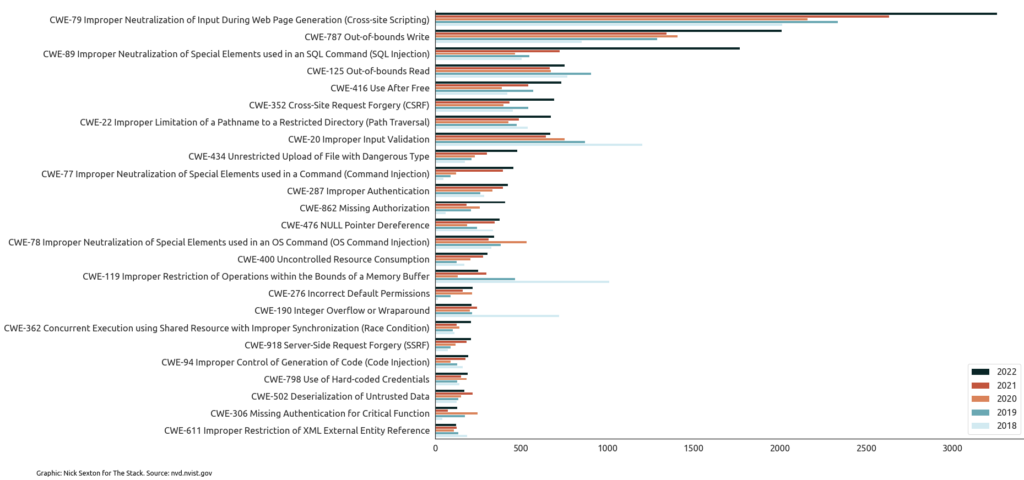
Earlier analysis by The Stack of Common Vulnerabilities and Exposures (CVEs) data revealed a record 26,448 software security flaws were reported in 2022, with the number of critical bugs up 59% on 2021 to 4,135.
Our review showed that well-known application security failure types remain rampant and continued to grow in 2022, suggesting a deeply inadequate focus upstream on basic fuzzing or security testing before products are released. This was reflected in the rise in frequency of many of the top 25 most dangerous Common Weakness Enumeration (CWE) types over the past five years, for example cross-site scripting (XSS) and SQL Injection weaknesses.
CISA requested nearly $425 million in its fiscal 2024 budget to build a Cyber Analytics and Data System to serve as a single internal repository for its analysts and to help prevent breaches before they occur. The agency has also been working with the Office of Management and Budget to develop a standardized self-attestation form for software providers to confirm their technology complies with supply chain security standards.









