In brief: Critical Citrix vulnerability under active attack. CVE-2023-3519 affects Citrix ADC and Citrix Gateway when configured (under a range of settings) as a gateway. CVSS of 9.8. Gives attacks unauthenticated attacks remote code execution (pre-auth RCE). Exploits detected in the wild. Patch asap.
Note: July 21 update with IOCs and more guidance here
Citrix has warned that a critical unauthenticated remote code execution vulnerability in Citrix ADC and Citrix Gateway is being exploited in the wild – a security advisory that will send chills down the spine of customers.
The pre-auth RCE Citrix vulnerability, allocated CVE-2023-3519, affects appliances configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or as an AAA virtual server, Citrix told customers on July 18.
The critical Citrix vulnerability has a CVSS of 9.8. It only affects customer-managed NetScaler ADC and NetScaler Gateway. (The names by which the products owned by Citrix are still broadly known.) Citrix-managed cloud services or Citrix-managed Adaptive Authentication are unaffected.
Citrix credited security researchers at Resillion with the finds.
The following products are vulnerable:
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.13
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-91.13
- NetScaler ADC 13.1-FIPS before 13.1-37.159
- NetScaler ADC 12.1-FIPS before 12.1-65.36
- NetScaler ADC 12.1-NDcPP before 12.65.36
Citrix vulnerability CVE-2023-3519: No IoCs for exploitation yet
“Exploits of CVE-2023-3519 on unmitigated appliances have been observed” the company said in a security advisory, adding that it “strongly urges affected customers of NetScaler ADC and NetScaler Gateway to install the relevant updated versions as soon as possible.”
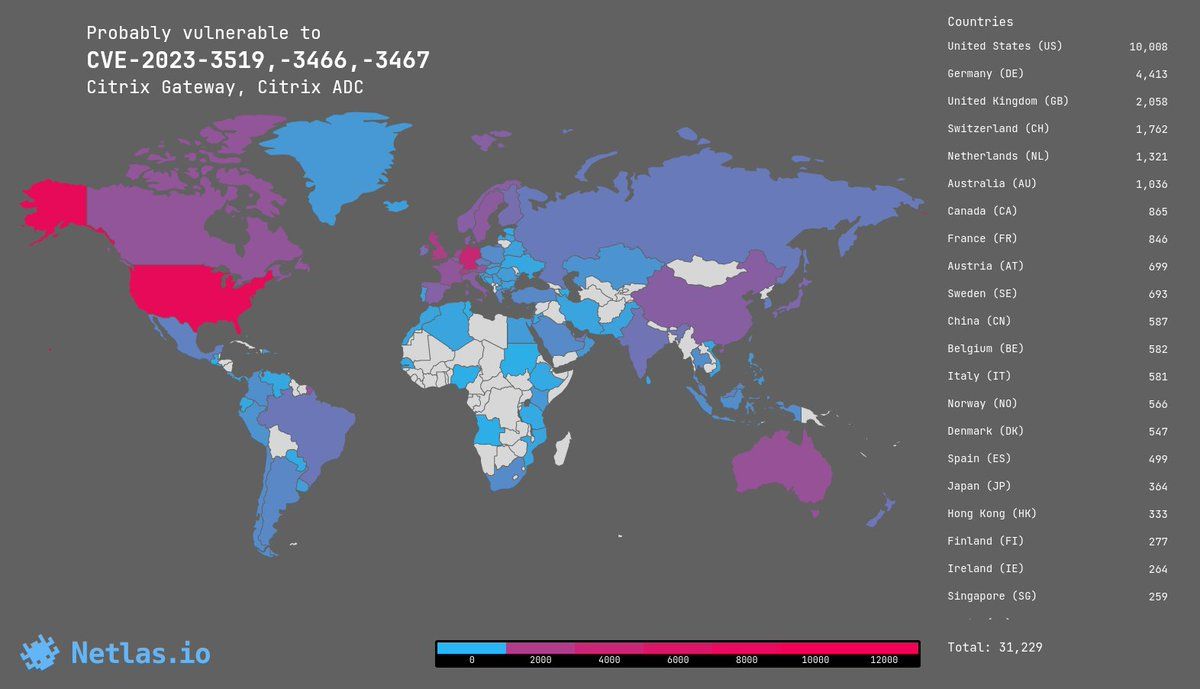
There are approximately 38,000 Citrix Gateway appliances exposed to the public internet. It was not immediately clear as The Stack published how many were exposed, based on their configuration [[updated July 20: Netlas estimates around 31,000]; or how widespread CVE-2023-3519 exploits are: Citrix has not published useful IOCs.
It is one of three vulnerabilities patched today that demand urgent attention from Citrix customers. The others are CVE-2023-3466 (CVSS X.X), a reflected XSS vulnerability—successful exploitation requires the victim to access an attacker-controlled link in the browser while being on a network with connectivity to the NetScaler IP (NSIP); and CVE-2023-3467 (CVSS X.X) which allows for privilege escalation to root.
As one security expert, Florian Roth noted on Twitter: “If a vuln is known to be exploited in the wild, the advisory shouldn't just contain info on affected versions and patches. It should also contain indicators that can be used to assess a system and find out if it has already been compromised.
“I think I'm stating the obvious here…”
More details as we get them.