Over a million Microsoft machines appear potentially exposed to a wormable critical new vulnerability, CVE-2022-26809 in Microsoft's ubiquitous remote procedure call (RPC) runtime library.
(RPC is as an inter-process communication mechanism for data exchange and functionality invocation in a different process -- a process which can be on the same machine, a LAN, or the Internet.)
Patched as part of a bumper Patch Tuesday and reported by China's Cyber Kunlun team, CVE-2022-26809 is a zero-click remote code execution (RCE) vulnerability that earned a CVSS score of 9.8.
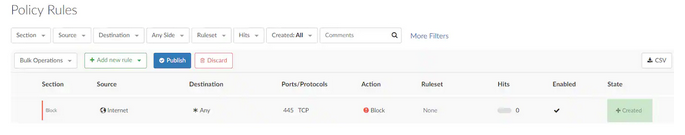
A public CVE-2022-26809 exploit is expected to land within days, if not hours -- offensive security professionals being the eager beavers that they are. Blocking port 445 at the perimeter is the start of mitigation.
Security researchers at Akamai have now compared versions 10.0.22000.434 (unpatched, from March) and 10.0.22000.613 (patched, from April) of the RPC runtime library in question within the Windows RPC runtime, which is implemented in a library named rpcrt4.dll -- and produced a detailed list of changes.
https://twitter.com/OphirHarpaz/status/1514358026668552197
These reveal that the CVE is an "integer overflow bug [that] could lead to a heap buffer overflow, where data is copied onto a buffer that is too small to populate it".
The two -- Ophir Harpaz and Ben Barnea -- added that calls to check for integer overflows were added in various functions including the following:
- OSF_CCALL::ProcessResponse
- OSF_SCALL::GetCoalescedBuffer
- OSF_CCALL::GetCoalescedBuffer"
The integer overflow vulnerability and the function that prevents it added as part of the patch exist in both client-side and server-side execution flows they noted in some rapid research published April 14.
Shodan/Censys searches show over 1.3 million publicly exposed instances of port 445 -- the one Microsoft urges in its patch guidance to block at perimeter. (It is unclear how many are "real" targets not honeypots.)
Security professionals fear a public CVE-2022-26809 exploit will land far faster than likely hundreds of thousands of organisations get it together to patch, as is too often the case. (One 2020 report by the Government Accountability Office revealed that federal US agencies given 45 days to patch a critical Cisco bug took six months to get halfway -- i.e. 50% were patched -- and two years to fully comply.)
Cyber Kunlun disclosed 35 Microsoft vulnerabilities to Redmond this month. Some security professionals fear that given Beijing's legal requirement to disclose vulnerabilities to the government its APTs could have had early sight of the vulnerability and potentially abused it.
Threat actors fight to exploit CVE-2021-26855 as row brews over POC
Blocking ports at the firewall "may be good practice, but is not feasible on the inside of the perimeter which is where this exploit could be used to much effect" Jamie Moles at ExtraHop noted in an email to The Stack, adding: " Wannacry spread laterally in networks using EternalBlue -- this would look very much the same"
Akamai's Ophir Harpaz and Ben Barnea added that admins should limit lateral movement by allowing incoming TCP port 445 only on machines where it is needed -- domain controllers, print servers, file servers, etc. Microsoft also urged customers in its advisory to use segmentation and isolation techniques to secure SMB traffic and reduce threats between devices on a network. SMB is used for file sharing, printing, and inter-process communication including RPC.









