Six Microsoft Windows vulnerabilities are being actively exploited in the wild and demand prompt patching.
Some of those exploited vulnerabilities like CVE-2022-41125 – frustratingly for IT security professionals overseeing large estates with demands for high levels of uptime – require system reboots to take effect.
They were among the 64 patches from Microsoft this November Patch Tuesday.
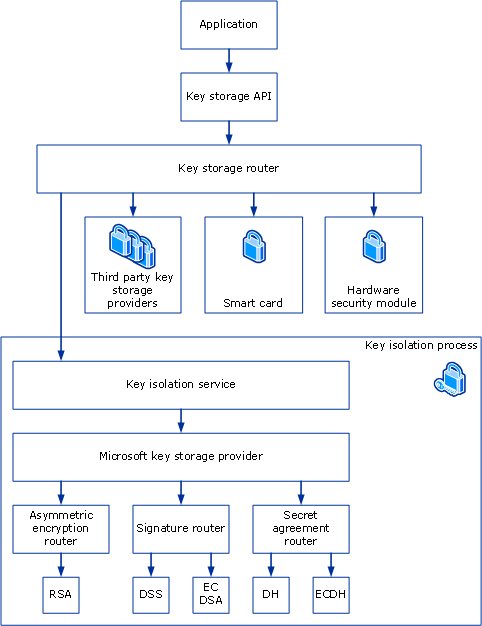
CVE-2022-41125 looks like one to prioritise: The elevation of privilege (EOP) bug in Microsoft’s cryptography API key store* requires local access, but only needs low privileges to exploit, requires no user interaction, and gives a successful attacker powerful SYSTEM privileges. Microsoft attributed the vulnerability disclosure to its own MSRC and MSTIC teams rather than an external disclosure, but says it has seen it exploited in the wild.
*The bug appears to be a memory overflow-related one. It’s in the cryptography API: Next Generation (CNG) Key Isolation Service – which runs as a LocalSystem and shares an executable (lsass.exe) with several other services. It stores keys to authenticate users in the Winlogon service, e.g. a wireless network key or the required cryptographic information for a smart card. CNG replaced the now deprecated CryptoAPI. In theory for a bad actor to exfiltrate a private key from CNG, they have to compromise LSASS, which runs as SYSTEM. We look forward to seeing some more intelligent analysis than ours in coming days as security researchers start exploring the bug.
CVE-2022-41125: Who’s abusing it?
Redmond gave no indication of how widespread abuse might be, nor did it share any Indicators of Compromise (IoCs). As patch management firm Automox’s Gina Geisel notes however: “With a long list of Windows 10 and 11 impacted (in addition to Win 8.0, 7.0, Server 2008, 2012, 2016, 2019, 2022, and 2022 Azure), this vulnerability exposes industry-leading versions of Windows and could have wide-ranging impacts”.
(As ever, well-resourced cybercriminals are typically ready to reverse engineer patches for critical or elsewhere-exploited vulnerabilities like these and weaponise themselves exceptionally rapidly – within days – intelligence services have warned over the past year – so judicious action is indeed encouraged.)
A fix for the vulnerability was among 64 new Microsoft patches released today, 11 rated Critical and 53 rated Important. They join the 22,000+ new CVEs allocated so far in calendar 2022, according to a quick review of NIST’s database by The Stack today. As ever the Zero Day Initiative has a good synopsis of some other priorities that we won’t regurgitate. Welcome patches for the widely exploited “ProxyNotShell” Microsoft Exchange Server bugs CVE-2022-41028 and CVE-2022-41040 and CVE-2022-41091 – an exploited vulnerability in Windows Mark of the Web (MotW) security feature affecting Windows 10, 11, and Server 2016-2022 stand out.
nb: Owing to the difficulty of effectively patching Exchange Server and the notable levels of exploitation of the ProxyNotShell vulnerabilities, if you did not mitigate early (this relied on the usage of a URL Rewrite rule to identify and block exploitation attempts as well as disabling remote PowerShell access for non-admins) and even if you did, a good hunt for IOCs would be sensible; the vast majority of security partners and vendors can support with this.









