A Five Eyes list of the most exploited vulnerabilities in 2022 has uncanny parallels with 2021’s list: 58% of the software security flaws on it made a showing in the previous year’s list also, emphasising what an uphill battle remains to encourage organisations to patch or mitigate against even the most ubiquitously abused and widely flagged cybersecurity risks.
The new list of the most exploited vulnerabilities in 2022 – published early August 2023 by CISA and partner agencies – hints at a change of focus: Not by hackers, who remain attracted to the low hanging fruit of critical vulnerabilities for which exploits and metasploit modules et al are easily available; but by government authorities, who emphasise in the very first call-to-action of the advisory that vendors need to perform better…
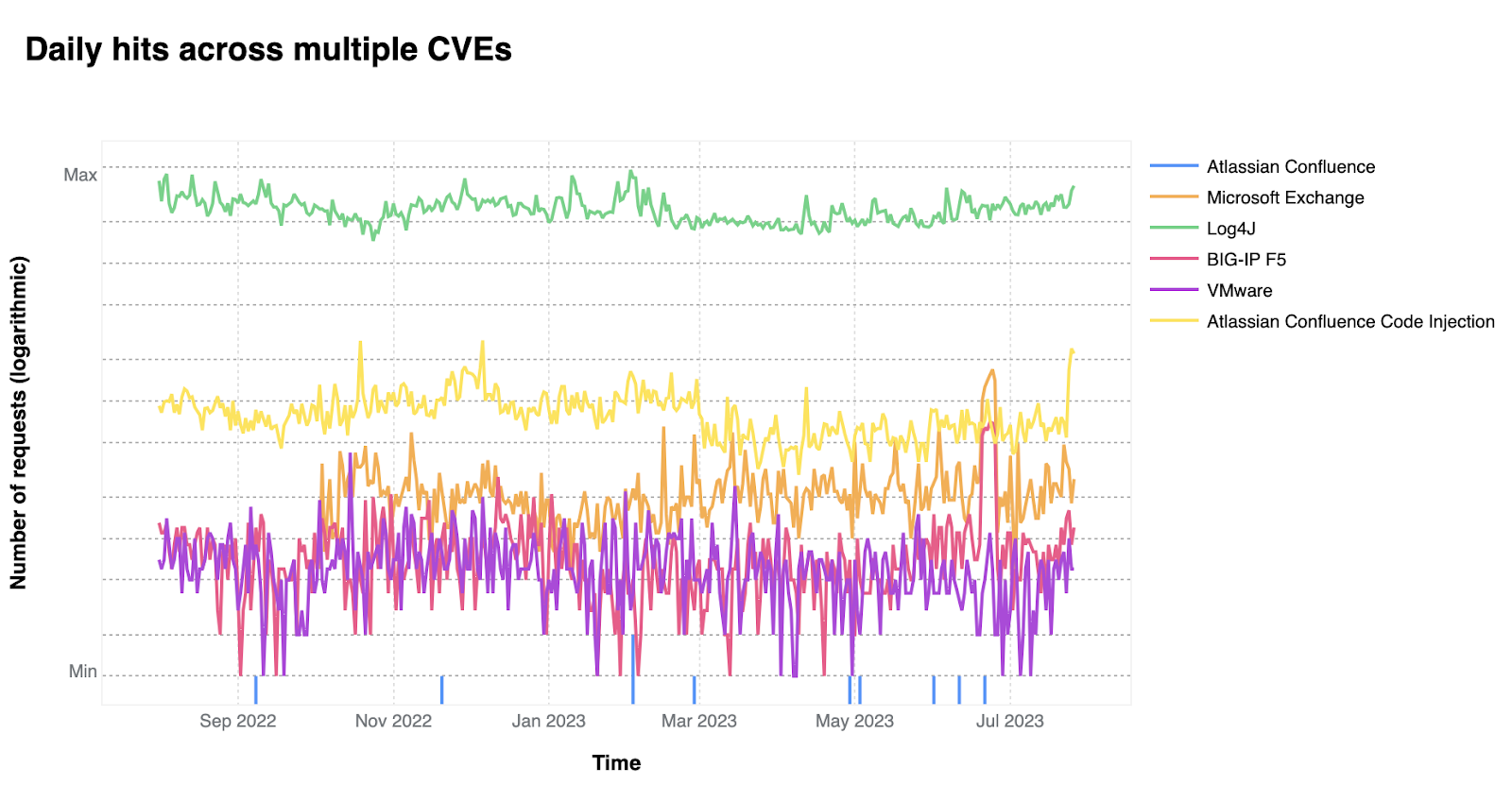
See also: Thousands of VMware customers publicly exposed to pre-auth RCE as exploit reproduced
“Vendors, designers, and developers [should] implement secure-by-design and -default principles and tactics to reduce the prevalence of vulnerabilities in your software…Follow the Secure Software Development Framework and implement secure design practices into each stage of the software development life cycle [and] establish a coordinated vulnerability disclosure program that includes processes to determine root causes of discovered vulnerabilities,” CISA and partners said; a notable addition given that 2021’s advisory did not even include the word “vendors”.
(The advisory’s early emphasis on demanding “secure by design” software suggests harks back to some of the key pillars in 2019’s cross-party US “Solarium Commission”, which had highlighted a need to “incentivize product manufacturers to scrap a ‘first to market’ mentality” and which warned industry bluntly that the “aggregated vulnerability assumed by [vendors] has created a significant national concern: rampant insecurity that passes costs of billions of dollars to downstream consumers and that has the potential both to disrupt our day-to- day life and to undermine public confidence in and the effectiveness of key institutions…”)
See also: Hyperscalers, telcos exposing BIG-IP to the internet as pre-auth RCE vulnerability drops
The Commission’s proposal that “Congress… pass a law establishing that final goods assemblers of software, hardware, and firmware are liable for damages from incidents that exploit known and unpatched vulnerabilities for as long as they support a product or service” looks unlikely to happen.
But the new list does suggest that vendors pushing out porous software without even the most rudimentary fuzzing and security testing may find themselves increasingly in the spotlight and possibly, hot water in future.
The 12 most exploited vulnerabilities of 2022
(CVEs in bold also featured in 2021's "most exploited" list)
Note: Exploit links shared for Red Team research purposes only and not tested by The Stack. Handle with care and always play safely in a sandboxed environment.
CISA warned that software companies’ business leaders should take “proactive steps to eliminate entire classes of security vulnerabilities, rather than… one-off patches when new vulnerabilities are discovered.”
The most exploited vulnerabilities in 2022 advisory from CISA urged vendors to “perform an analysis of both CVEs and known exploited vulnerabilities to understand which classes of vulnerability are identified… Implement appropriate mitigations to eliminate those classes of vulnerability [e.g] if a product has several instances of SQL injection vulnerabilities, ensure all database queries in the product use parameterized queries, and prohibit other forms of queries… [use] static and dynamic application security testing tools to analyze product source code and application behavior to detect error-prone practices.”
The full advisory is here.








