CISA has urged Sisense customers to “reset credentials and secrets” after a serious data breach at the business analytics software company.
The incident has had potential downstream impact on the security of critical infrastructure sector organisations, CISA suggested.
The incident appears to have exposed the plaintext storage of customers credentials by Sisense, according to one security researcher.
Supply chain risk?
Sisense integrates with a range of enterprise data sources like databases, spreadsheets, cloud services, and web applications. Any compromise exposing credentials could potentially be ridden downstream by attackers.
As Marc Rogers, a former CISO, now head of security at DEFCON put it on X: “[Sisense] require access to their customers confidential data sources.
Sisense breach: "Treat as an EXTREMELY serious event
“They have direct access to JDBC connections, to SSH, and to SaaS platforms like Salesforce and many more. It also means they have tokens, credentials, certificates often upscoped. The data stolen from Sisense contained all these tokens, credentials and access configurations. This is a worst case scenario for many Sisense customers. These are often literally the keys to their kingdoms. Treat as an EXTREMELY serious event.”
It was not immediately clear what the dwell time of the attackers was.
I would like to shout out the amazing collaboration of @cybercentre_ca @CISAgov @NCSC @ncsc_gov_ie @fbi NCSC NZ @CERTNZ and Antartica CERT (and many other individual agents) who came together to help a bunch of nerds contain the Sisense breach. From the community - THANK YOU!
— Marc Rogers (@marcwrogers) April 11, 2024
Sisense was founded in Israel in 2004. It has offices in New York City, London, and Tel Aviv and names customers like Verizon and PagerDuty.
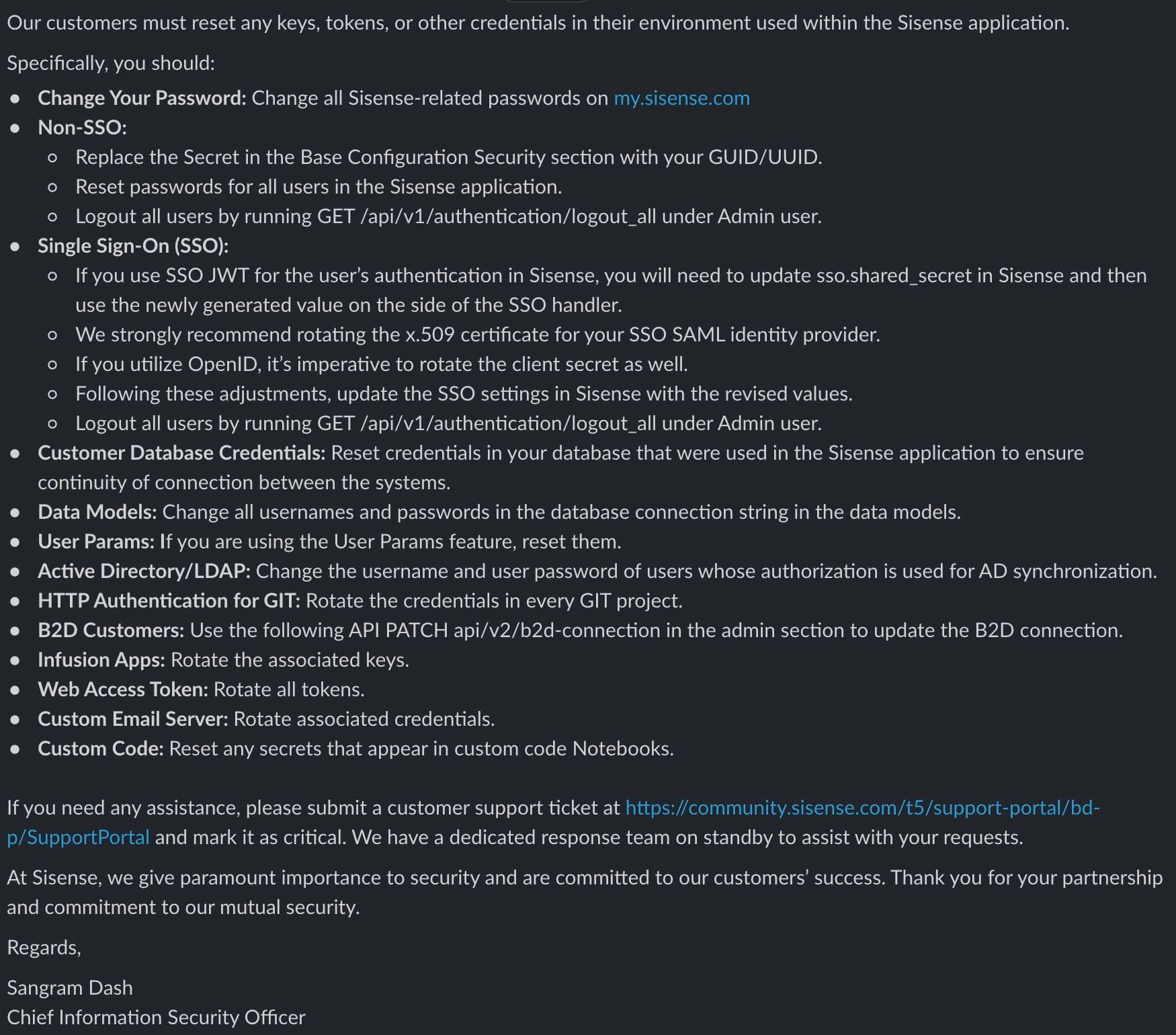
Sisense CISO Sangram Dash has now shared explicit instructions for Sisense customers, shown embedded above. More details to follow.









