Containerisation has underpinned agile innovation and turbocharged businesses’ digital capabilities - but for CIOs, CISOs and their teams, it has also been a huge visibility, management, and security challenge.
Microservices-based applications managed using containers are increasingly ubiquitous – yet as they are typically distributed over multiple data centres, cloud providers, and host machines, visibility can be challenging.
As decoupled application components communicate over multiple different infrastructure layers and require myriad entry points to both internal and external stakeholders, the threat surface also grows.
It is easy to lose track, particularly as 72% of containers live less than 5 minutes, and bad actors operate equally quickly. (Expose a Docker API in a honeypot, for example and malicious images land rapidly.)
Take Chimaera, a campaign first spotted in 2021 that installed cryptocurrency-mining malware on vulnerable Docker containers. Around 10,000 new container images are uploaded to Docker every day, making it incredibly hard for IT teams lacking the right tools to spot the compromised images that hijack their software.
Yet missing them is costly: cloud and contain security specialist Sysdig found that the cost of mining one Monero coin (XMR) on a single AWS EC2 instance is roughly $11,000. That’s an expensive risk, even before taking into account the potential for data breaches or downtime caused by malicious but unseen activity.
https://www.youtube.com/watch?v=GhivqT3jV1Q
Container security: Everything, everywhere, all at once
Sysdig Founder and CTO Loris Degioanni – the creator of open source runtime security tool Falco, which has been downloaded over 37 million times since 2020 – founded Sysdig as an answer to the unique visibility and security challenges of cloud-native and container-centric IT environments.
The company’s open standards-based approach and cloud-native experience has won it a growing customer base that now includes Cisco, Goldman Sachs, and McKinsey among others. What has made it so successful?
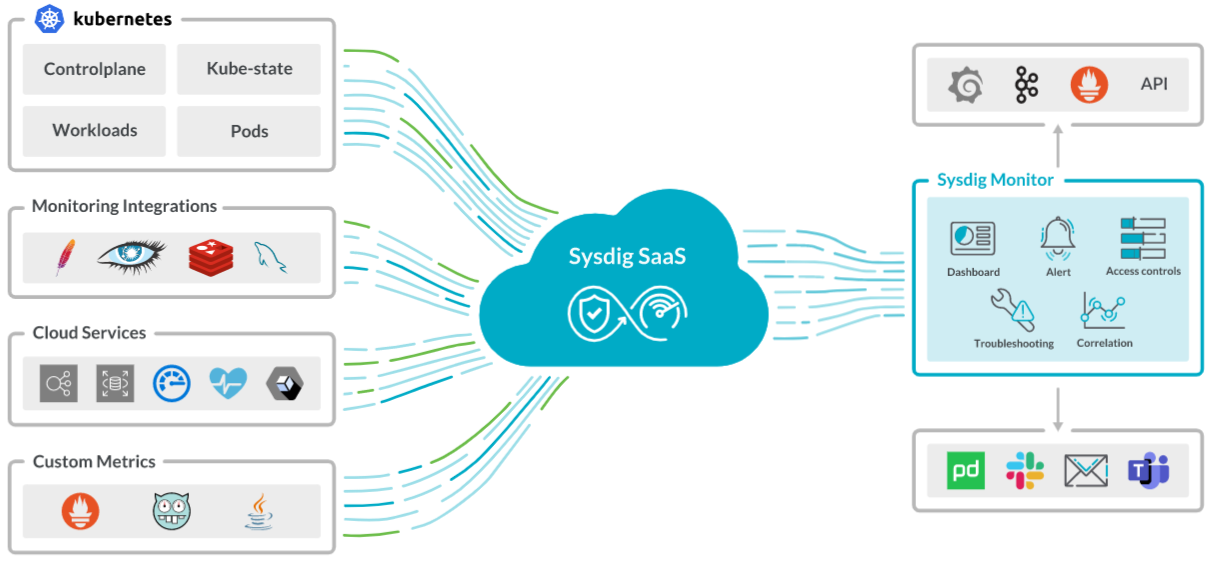
Degioanni’s initial focus was on creating an open source monitoring tool called Sysdig Open Source, which the company then built additional troubleshooting, cost-optimisation, and alerting functions on top of to launch Sysdig Monitor. Sysdig then tackled security by creating Falco, the open source standard for real-time detection of threats and anomalies across containers, Kubernetes, and cloud services. In 2018, the company launched Sysdig Secure, which is built on Falco. In addition to threat detection, it offers automated remediation capabilities that gives users process-level visibility into dynamic, distributed production environments.
With a simple lightweight agent, it proactively alerts on incidents across services, hosts, containers, with support for further offline troubleshooting and forensics. It extends this deep visibility into Kubernetes clusters, namespaces, workloads, pods, and containers across cloud platforms (AWS, Azure, GCP, and IBM).
CCTV and rapid reaction squads, not drawbridges and moats
Most IT professionals will be wearily familiar with conversations about the demise of “moat and castle” cybersecurity (in which “your” software runs in “your data centre” inside the castle and routes in and out are limited and tightly restricted. Degioanni extends the metaphor compellingly however, describing modern architectures as less a castle and more like a sprawling “city with thousands of highways that go in and out.”
You simply cannot wall off a modern city, or IT architecture.
“People from all over all over the world come and connect to your software, but also everybody inside the company needs to go in and out to make changes, send releases, update the software” as Sysdig’s CTO puts it to The Stack. To extend the metaphor, rather than a guard, you need high resolution CCTV and rapid reaction units.
You also want that CCTV to be high-resolution. Sysdig’s granularity is such that its sensors record every interaction between a container and another piece of software, whether that’s closing a file, or establishing a network connection, with the Sysdig Secure platform, assessing millions of system calls a second for threats.
It also checks external sources, such as logs coming from cloud providers or open source platforms such as GitHub – but rather than overloading systems with expensive-to-store logs, its guiding philosophy is to detect threats “in a streaming way” making it quicker to identify threats and report them, but also to offer a more cost-effective alternative to warehousing all of the data. By doing this “you have less bandwidth costs, you have less storage costs, you have less indexing, an less CPU costs,” Degioanni notes; alerts are highly configurable.
The company introduced image profiling with machine learning back in 2019 that also helps reduce false positives and its approach to runtime defence in large-scale environments is to automatically model runtime behaviour by analysing this activity inside the containers: “Analysing syscalls, traversing the kernel leveraging eBPF technology and enriching them with various metadata including Kubernetes and Cloud provider labels, allows Sysdig to create a truly comprehensive container runtime profile” as the company puts it.
"We have something that is blessed by the community, that is lightweight and secure"Sysdig CTO Loris Degoianni
“These are all extremely important sources of information, and we’re able to bring all of them together and put them in a single place,” says Degioanni, adding that open source is at the heart of Sysdig’s security philosophy.
The Sysdig CTO says it influences everything from using a common language (Falco) to how its applications are instrumented. “The way we instrument for security doesn't require us to put out 25 different agents. We have something that is blessed by the community, that is lightweight and secure,” he explains: “There is a flourishing ecosystem on top of that, and we can get contributors from all over the world. Sysdig is well integrated with the rest of the open source computing stack, like Kubernetes, Prometheus and service meshes and so on.
He adds: “When you think about the modern computing stack for the cloud, based on containers, based on Kubernetes, based on all of the different pieces of software infrastructure, like networking, and so on, they are all based on an open stack. Security has been lagging. But I argue that it's even more important for security to be open: We are fighting a war with the bad guys, we can only hope to win this war, if we fight it together.
“Without having the security truly embedded in the rest of the open source stack we will never have true security in the long term. That’s why we started Falco, the runtime security tool, and why we also sponsor Wireshark. [The hugely popular open source network analyser, which Degioanni also co-created]. This gives us a unique perspective, compared to the many security vendors that are more siloed in their own technology.”
He concludes: “I am convinced that the future of security is open.
“That will help developers and security teams massively when they want to understand what is going on with a security risk or broader visibility into issues. ‘Where was this? Which country? Which region? What service? Was this in production? Was this in a development environment or one containing sensitive data? Which developers should be notified?’” That’s where Sysdig comes in – and it’s been a community effort.
Sponsored by Sysdig









