Benjamin Harris hated school and spent a lot of time tucked away in the library. One day he read a story about a teenager breaching the Pentagon from a home desktop and “something just clicked.” On a call with The Stack he recalls how he spent the next few years going down a well-trodden route that can be summarised as “teenager has computer, will hack voraciously, get into deep trouble with The Authorities" and which sometimes ends in prison, sometimes in entrepreneurial glory.
Twists of fate, strong character, or helpful family: Whatever it was, for Harris those boundaries-testing online escapades resulted in school expulsion rather than anything worse. With an ultimatum from his family that he get a job within a fortnight or find somewhere else to live, he steered his burgeoning offensive security talents into consulting work for security testing firm Portcullis; later joining F-Secure as a technical director before that questing, entrepreneurial streak won out.
Turns CEO…
Harris is now CEO of watchTowr, a Singapore-headquartered startup that he founded in 2021; in 2022 raising $8 million in a pre-series A round.
The company provides automated threat surface mapping and vulnerability hunting – letting customers know, for example, that they have X number of Ivanti or Fortinet boxes online exposed to Y new critical vulnerability that is already seeing exploitation in the wild.
See also: Fortinet patches MORE pre-auth RCEs, with exploits reported. Ivanti also slips out a fresh VPN fix...
It aims, in short, to act as an always-on, agentless scanner for anything publicly exposed for customers; replicating early-stage hacker activity, then identifying what is vulnerable to exploitation and needs fixing.
It also does its own analysis to inform this activity.
watchTowr has been catching infosec professionals’ attention in recent months with some incisive security research focused on a growing flurry of vulnerabilities in SSL VPN appliances (network gateways that provide an encrypted connection between the public internet and a corporate or institutional network) and The Stack decided to pick up the phone.
We sat down to talk evolving attack surfaces, the rise of identity/credentials-based breaches, Red Team scoping/automated platforms and more. (Our Q&A has been lightly edited for legibility, brevity.)
What does watchTowr actually provide?
"We focus on [identifying] exploitable validated vulnerabilities; things that an attacker could credibly use against an organisation: an RCE in a Fortinet VPN appliance, for example; a Log4Shell instance; all the way through to data or credentials exposure on databases and SaaS platforms that we can use to log into a VPN or a JIRA instance, etc. So things that are material [for defenders] in terms of actually improving security posture.
"From a tech perspective, to be able to do that we have three primary engines. [Firstly we identify] what does this organisation have exposed to the internet, not just in terms of servers, but cloud environments, SaaS platforms, containers, mobile apps; we can then also very clearly catalogue what technology they use everywhere – so we have a very clear living picture [of] what every client looks like on the internet; what do they actually have exposed? What would be of interest? [To a hacker.]
"Our second engine takes that picture and basically says ‘how do we break in?’ That's a collection of broad spectrum tactics and techniques aligned to industry standards like MITRE ATT&CK; taking credentials off the dark web and demonstrating that they can be used to log into an exposed Microsoft Active Directory instance, all the way through to looking at how do they actually configure DNS and how they're using CDNs…
"The third part is how do we rapidly react? The number of vulnerabilities is exploding. One thing the industry has really focused on and really aligned on is this idea around prioritisation. Not all vulnerabilities were created equal. If you look back 10 years ago, an attacker would take three to four weeks to weaponise a vulnerability – to go from announcement to ‘I can now use this to break into my target.’ In the last two, three years, we've seen ransomware gangs basically appreciate that the faster they get into an organisation, the more likely they can turn that into a ransom.
“Exploitation happens in four hours. So whatever size organisation you are, you’ve got four hours to work out if you're exposed. So that first engine is basically our adversary sight. It’s ‘what does the organisation actually look on the internet right now?’ Every hour, we refresh what we think every client looks like on the internet, the same way attackers do.”
Red Teaming can fall down pretty fast on scoping restrictions; i.e. when an organisation says “oh you can’t scan/test that because it will fall over.” Do you find that affects customer appetite for your capabilities?
"I think we have to accept that what we're doing is very much forward looking in terms of where we think industry will go. Unless organisations move to this approach, they are going to be fighting breaches in the same way they've been doing for the last five years, for the next five years.
“So every organisation that we work with, ranging from literally Fortune 100, all the way through to some of APAC’s largest regional banks, have basically said, ‘we appreciate now that this kind of scoping mechanism approach doesn't make sense’ I think we have to remember as well, that scoping concerns have always come from different perspectives in organisations: They've come from ‘can I afford to do a big scope?’ They've come from does the app team really want the entire scope in this particular assessment? When we engage very senior level [clients] in our business, we explain to them ‘these are the challenges you're definitely facing already; this is what we need to do: act like an attacker not like a pen tester, not like a network architect. What does the attacker see? What would the attacker do to target you? Most of our clients, when they come to us don't know what they’ve got exposed… so we typically in-scope entities, like legal entities, as opposed to IP ranges or domains."
The threat surface is evolving fast. We’ve talked about the greater pace of vulnerability exploitation but social engineering is also increasingly rife. What do you see changing; how has this landscape changed?
"I would say that 5-10 years ago, every team had that spreadsheet of IP addresses, domains and subdomains in their IT department folder on their local Samba drive and went ‘okay, that's what we'll track for the next 10 years coming.’ That static approach to assuming what people has not scaled, as you can imagine! A shadow IT problem has really exploded…
"Trivially, you’ve got a marketing team in Country B and region A that doesn't talk to a team in the UK, for example… stuff never gets updated and becomes vulnerable very quickly. Then there’s the cloud environments that you can spin up with just a credit card or a free trial, etc. all the way through to the things like GitHub, Postman Workspaces.
"We're seeing [as a result] a massive trend; a significant proportion of the daily ways to break into organisations are no longer vulnerability-based.
"We regularly for example will find exposed credentials in a SaaS platform, or a community repository that we can just use to log into a VPN. The identity is almost the attack surface..."
What’s driven that shift?
"With things like phishing, to be very frank, I think there was a lot of money to be made in solving that problem and finally, we made progress on EDR controls, MDR controls… mail gateway filters, proper sandboxing; it’s actually working. In 2022 [as a result we saw that] exploiting something in the perimeter was a more common entry point than phishing, for example. Targeted attacks have really shifted into the exploitation of external device, external perimeter. Everyone's bought EDR agents and deployed them everywhere, whether that’s CrowdStrike, Palo Alto, etc, etc. But the SSL VPN appliances, you can't deploy any protection on, they are black boxes, unknown to the wild, you can compromise one, you can sit there completely anonymous."
You’ve made a bit of a name for yourself recently poking holes in some of those appliances, e.g. Ivanti CVE-2024-22024. In a recent blog WatchTowr noted that you hate SSLVPNs: “They all appear to have been constructed with the code equivalent of string, stamped with the word ‘secure’ and then just left to decay for 20 years.” Why are their builds often so insecure?
"A lot of them were built from the ground up about 15-20 years ago. Being black magical boxes that nobody really sees inside of, there hasn't been a huge amount of pressure by anyone on any vendor… people have just been buying them, truckload after truckload, and there’s a significant cost attached to them. You've then got organisations that aren't necessarily keeping up to date on the latest branch. You’ve got FortiOS 6, 7, 8 in production: six is like 10 years old at this point and is still being run in production. That’s not necessarily Fortinet’s fault of course…"
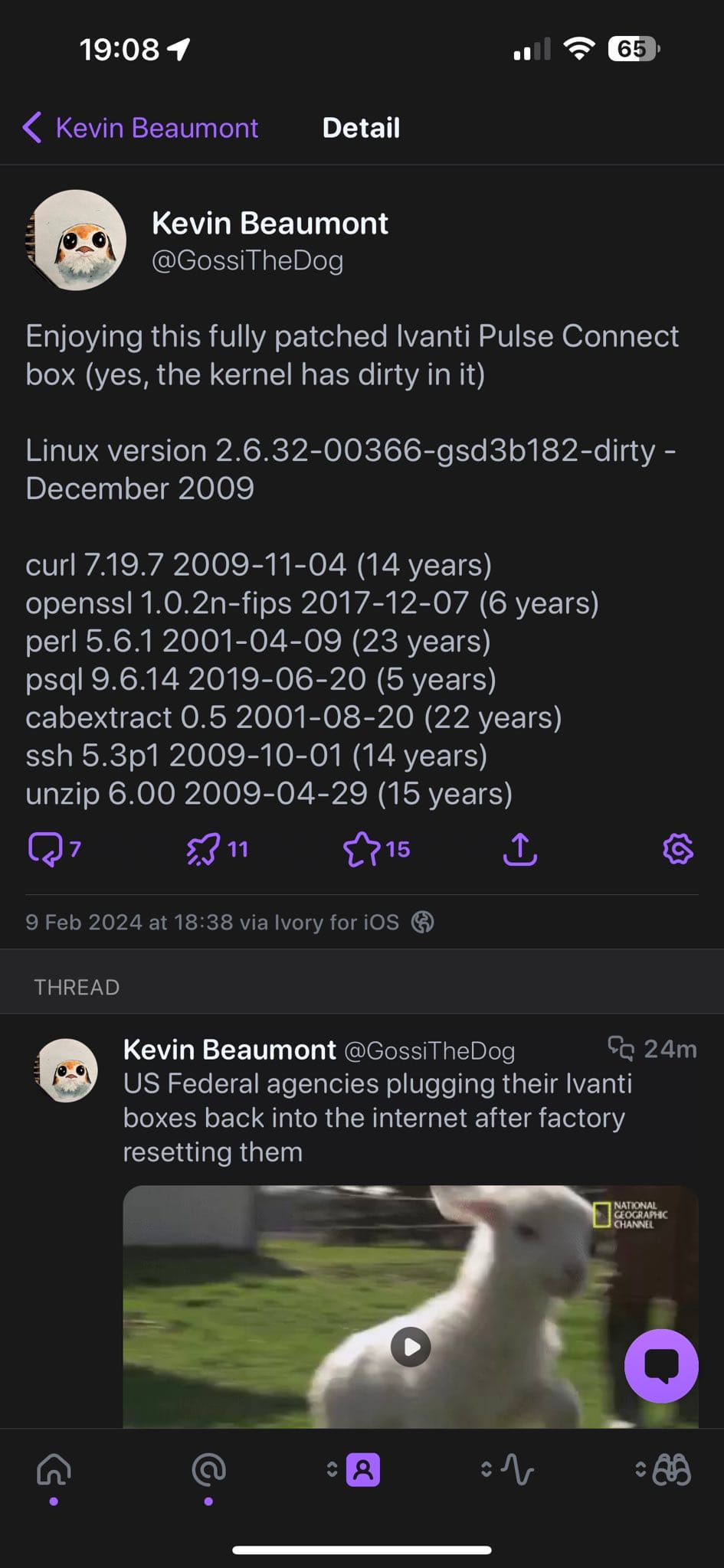
"With Ivanti, it's genuinely surprising to see an appliance that costs so much money and holds such a critical position in big enterprise environments be running software that has got 2007 dates on it. If we look back to the first Ivanti vulnerabilities being exploited in the wild this year, they were literally because there was a known library vulnerability reported last year that they never updated [in their products.]"
[Ed: Tracked as CVE-2024-21893, a Server-Side Request Forgery (SSRF) vulnerability in the SAML component used by Ivanti Connect Secure, Policy Secure, and ZTA gateways has been exploited in the wild this year. It has its roots in a bug in the xmltooling library, patched out around June 2023 and assigned CVE-2023-36661 that can be chained to an Ivanti bug for unauthenticated command injection with root privileges.]
Is the answer to this partly just rip out these legacy VPNs and move to “Zero Trust” or SASE alternative?
In Gartner's mind, everyone's moving away from VPNs; VPNs don't exist anymore! I think the reality is that for anyone over a 10-person organisation, this is not a ‘rip out an appliance, and then shove something else in.’ It's a major re-architecture of how they manage devices, manage files, whether they keep those and especially with regulatory compliance in some of these organisations around where that data goes, it isn't as simple as just saying, ‘’chuck it in the cloud and call it a day…’
“We have multiple clients that literally have hundreds of Ivanti appliances in their attack surface; for them to rip things out across literally hundreds of thousands of employees? Not super simple…
"But I think you can almost see the fear in some of the advisories have come out from different VPN vendors in the last kind of couple of weeks, because it's gone very much from ‘there's a vulnerability; we release a patch at some point in a few days, we'll give you some mitigation advice’ which was probably useless at that point. But it's gone to ‘our internal teams are looking for more bugs, we swear we're looking for more bugs, we promise we'll find more bugs!’ it's clearly defensive-sounding now…”
Any particular founding moments that stand out?
Watching things scale out [has felt great.] We measure success by how many assets we look at every hour; at this point, we look at millions and millions of systems on behalf of clients every single hour.
"To be able to do that Ivanti [vulnerability] research so quickly, and then scale it out to all of those systems in literally an hour and tell a significant number of clients ‘a: You’re affected and these machines are the ones affected and b: Here's what you should do right now’ [was really helpful for customers]. I think this [level of pace and insight] is becoming more important, because we're now seeing a cyber insurers move up to the plate, saying ‘have you heard of Ivanti? What have you done [about this vulnerability]? What are you going to do to ensure you don’t have a claim in three months’ time?’ So the industry has really moved and using technology to scale that is quite exciting.”









