The UK’s National Cyber Security Centre (NCSC) started using honeypots in late 2022 to identify the sources of brute force attacks against common protocols and take down their infrastructure with the power of the state.
The NCSC’s Active Cyber Defence (ACD) programme, launched in 2017 to help tackle commodity-style attacks including phishing campaigns, started using the honeypots (network-attached systems set up as a decoy to attract and then study attacks) in August 2022, an annual report revealed.
It's the latest step by an increasingly proactive NCSC in tackling cybercrime – and follows on the back of the decision in late 2022) to start scanning all internet-exposed devices hosted in the UK for vulnerabilities. (All connections are made from one of two IP addresses: 18.171.7.246 or 35.177.10.231 and scanning is conducted using the open source nmap utility.)
NCSC honeypots are targeting brute force attacks
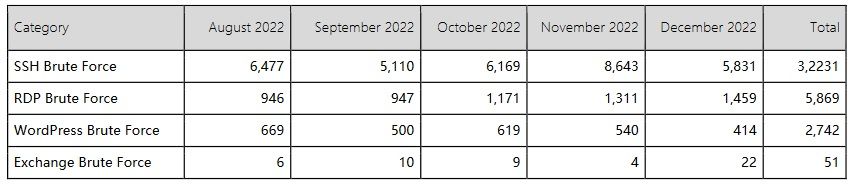
The NCSC honeypots identified over 32,000 SSH brute force attack attempts over the last five months of 2022 and over 5,800 RDP attacks.
It also captured brute force attack attempts against Wordpress (2,742).
(The ACD annual report does not specify how many specific takedowns resulted from the honeypot activity but The Stack has asked the question of the NCSC and will update this article when we receive an answer.)
SSH servers are a common target for brute-force attacks. (SSH is a cryptographic network communication protocol that lets users access, control, and modify servers over the internet. It is typically used as the primary means of connecting to Linux servers remotely. One way to mitigate ubiquitous automated brute force attacks is to reduce the number of authentication attempts permitted by a connection; e.g by trimming the MaxTries variable in the sshd_config file from its default of six, but speak to your security provider/team/partners to approach this best.)
Amazon, Cloudflare, GoDaddy named….
The NCSC, part of signals intelligence and cyber agency GCHQ, said it also took down 24,407 web shells in 2022 (“created by attackers using malicious scripts to install control panels on compromised servers”).
It named some well-known brands as the “most prevalent” hosts with the top five hosts of web shells being Newfold Digital, Cloudflare, GoDaddy, NameCheap, and OVH. Amazon and DigitalOcean also made the top 10.
The ACD report aso reveals that the NCSC took down over 150 extortion email campaign servers EVERY HOUR in 2022 under the ACD programme.
Follow The Stack on LinkedIn
As well as smashing these 1.3 million extortion email servers, ACD also took down malware infrastructure every 30 minutes (18,337 times).
Overall takedown numbers across the range of malicious cyber activity that the ACD targets fell however in 2022 year-on-year. The NCSC attributed this to a fall in the number extortion mail servers (down 528,000) and cryptocurrency investment scams (down 459,000).
It said: “These two attack types have some of the shortest uptimes on average, which could explain the reduction in prevalence as attackers concentrate on areas where their return on investment is greater. Mail servers and cryptocurrency investment scams have a median availability of 25.5 and 1 hour respectively. The next top 5 attack types are fake shop, phishing URL, brute force attack, web shell and malware infrastructure URL. Contrastingly, they have a combined median of 56.29 hours.”









