In brief: Western Digital hacked. Attackers have accessed multiple systems. Services down.
“The best time to back up was yesterday. The second-best time is right now” said Western Digital on March 31.
Customers will be hoping that the data storage specialist eats its own dogfood, after it admitted suffering a cyber incident that “has caused and may continue to cause disruption to parts of [its] business operations.”
An unauthorised attacker has accessed “a number of the company’s systems” Western Digital said April 3.
That has triggered a major outage of its storage services (which the company promotes as delivering “easy, efficient, secure cyber protection… award-winning backup with an AI-based defense against ransomware…”)
Western Digital, which sells storage devices to customers globally including cloud hyperscalers, is a big target: It reported revenues of $18.7 billion in 2022, with cloud storage revenues representing 42% of its total revenues.
Without explicitly saying so, Western Digital suggested that the attack may have been a ransomware incident.
“On March 26, 2023, Western Digital identified a network security incident involving Western Digital’s systems. In connection with the ongoing incident, an unauthorized third party gained access to a number of the Company’s systems. Upon discovery of the incident, the Company implemented incident response efforts and initiated an investigation with the assistance of leading outside security and forensic experts” it said on April 3.
“The Company is implementing proactive measures to secure its business operations including taking systems and services offline and will continue taking additional steps as appropriate. As part of its remediation efforts, Western Digital is actively working to restore impacted infrastructure and services” the company added.
We analysed 90,000+ software vulnerabilities: Here’s what we learned
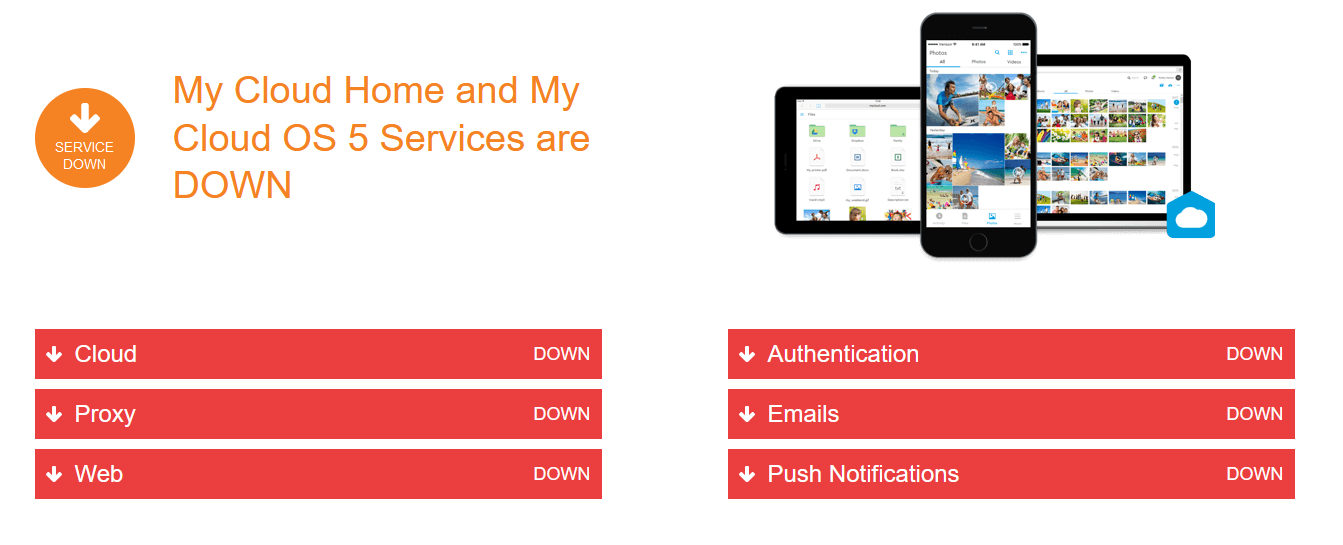
Customers are facing sweeping service outages, including across network attached storage (NAS). “Western Digital is currently experiencing a service outage impacting the following products: My Cloud, My Cloud Home, My Cloud Home Duo, My Cloud OS5, SanDisk ibi, SanDisk Ixpand Wireless Charger” its status page says.
The incident comes amid a fresh wave of ransomware attacks and other malicious security incidents. Major outsourcer Capita is currently also suffering from what it has now admitted was a security incident (after earlier referring to it as an "IT issue" and "technical problem") saying today (Monday April 3) that it "experienced a cyber incident primarily impacting access to internal Microsoft Office 365 applications... This caused disruption to some services provided to individual clients, though the majority of our client services remained in operation,” Capita added.
Western Digital hacked: Restoring from backups isn't always easy
As Secureworks’ Alex Papadopoulos, Director, Incident Response Consulting recently noted in The Stack, post-incident “recovery is crucial But it’s not as simple as some might think… Imagine, a threat actor has gained access to your network. The likely scenario is that they have full administrative access to your Active Directory.
With domain admin level access, they have the keys to everything, including your back up. We see adversaries head straight for the backups, which they destroy, before they go ahead and do the rest of the damage. They don’t want you to have a quick recovery plan and they know backups are core to that.Best case scenario, you have your backups intact. Have you actually tested how long it will take to restore everything? If you have a fully bricked system you will need to start by reinstalling the operating system first, then applications and services, before being ready to restore any data from backups – what we call a bare metal restore.
The reality is that restoration can take significant time to achieve.
[As an example one client] suffered a serious ransomware incident. In this case, they felt the ransom payment demand was something they could and should pay. So they paid it out on day one and got the decryption key.
But the ransomware had impacted most servers in the business. More than 5,500 servers were affected. In this case resource was not an issue. They hired staff where they needed them and supported the efforts financially as necessary, with the single goal of getting the business fully operational as quickly as possible.
Even with unlimited resources, it took three months to get them 95% recovered – and that was the most they could achieve, as some systems had been corrupted and could not be recovered… In another incident response engagement, the impacted organisation had backups which survived the intrusion and ransomware. What didn’t survive was the victim’s Active Directory. Functionally, they couldn’t even start the process of restoring because their backup solution required Active Directory to log in. They needed to authenticate, and nothing worked. It’s a basic building block, but one that requires specialist expertise which they did not have inhouse.
So even though they had backups, there was no way of using them…”









