A group tracked by Google's Threat Analysis Group (TAG), dubbed "EXOTIC LILY" has been sending up to 5,000 phishing emails each day with a comparatively unusual attention to detail-- including using domain and identity spoofing and creating fake personas with AI generated faces to pose as employees of a real company).
The group, which TAG said is acting as an access broker for ransomware groups, is also using legitimate file-sharing services like WeTransfer, TransferNow and OneDrive to deliver the payload undetected by security tools looking for potentially malicious emails. (The malware delivered then fetches Cobalt Strike payloads, TAG said.)
EXOTIC LILY was first spotted exploiting a Microsoft zero day (CVE-2021-40444) in September 2021. Within months the "resourceful, financially motivated group" started impersonating real company employees by copying their personal data from social media and business databases such as RocketReach and CrunchBase.
(CVE-2021-40444 -- check you are patched -- impacts Microsoft MHTML, a software component used in Internet Explorer but also used in Office applications to render web-hosted content inside Word, Excel, or PowerPoint documents; attackers typically craft a malicious ActiveX control to be used by a Microsoft Office document that hosts the browser rendering engine in order to exploit the widely attacked RCE bug.)
EXOTIC LILY threat group use spoofed domain names
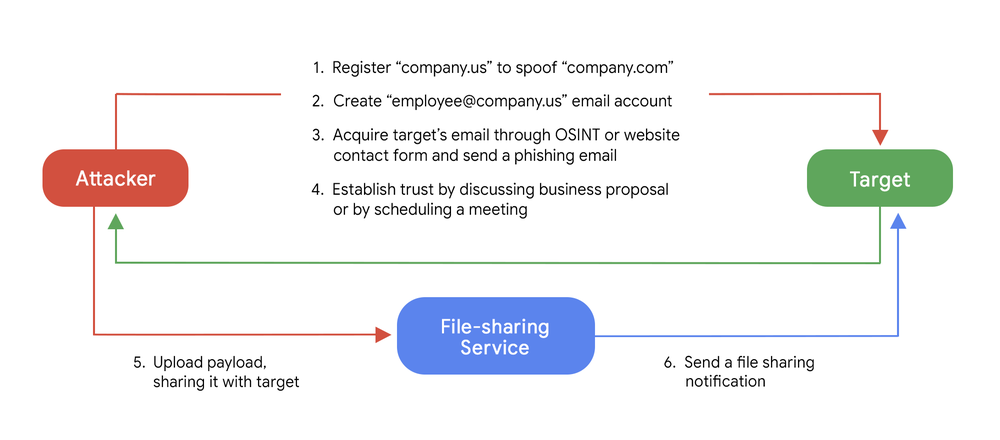
Describing the EXOTIC LILY group as likely to be access brokers ("the opportunistic locksmiths of the security world") for ransomware groups, TAG said at its peak in November 2021 the group was hitting 650 targeted organisations globally (specifically naming IT, cybersecurity and healthcare companies as targets) "but as of late we have seen them attacking a wide variety of organizations and industries, with less specific focus."
"One notable technique is the use of domain and identity spoofing as a way of gaining additional credibility with a targeted organisation. In the majority of cases, a spoofed domain name was identical to a real domain name of an existing organization, with the only difference being a change of TLD to “.us”, “.co” or “.biz” TAG said.
(One of the mostly alarmingly effective attacks The Stack has had described to us was by a Red Team professional who set up mail servers for typo-squatted domains at the cost of some $20, started catching every email aimed at a pharmaceutical company and within a week had received an email from someone on the "inside" of the company wanting IT support. The Red Teamer simply picked up the phone, said they had received the email -- "how can we help"? -- installed a remote access tool with the target's blessing: game over.)
Follow The Stack on LinkedIn
"Although the group came to our attention initially due to its use of documents containing an exploit for CVE-2021-40444, they later switched to the delivery of ISO files with hidden BazarLoader DLLs and LNK shortcuts" TAG said: "These samples have some indicators that suggest they were custom-built to be used by the group. For example, metadata embedded in the LNK shortcuts shows that a number of fields, such as the “Machine Identifier” and “Drive Serial Number” were shared with BazarLoader ISOs distributed via other means, however other fields such as the command line arguments were unique for samples distributed by EXOTIC LILY."

"In March, the group continued delivering ISO files, but with a DLL containing a custom loader which is a more advanced variant of a first-stage payload previously seen during CVE-2021-40444 exploitation. The loader can be recognized by its use of a unique user-agent “bumblebee” which both variants share.
"The malware, hence dubbed BUMBLEBEE, uses WMI to collect various system details such as OS version, user name and domain name, which are then exfiltrated in JSON format to a C2. In response, it expects to receive one of the several supported “tasks”, which include execution of shellcode, dropping and running executable files. At the time of the analysis, BUMBLEBEE was observed to fetch Cobalt Strike payloads."
TAG has some IOCs and more details here.
As well as the standard roster of tools and techniques to introduce friction for attackers defenders should consider using tools like BloodHound to map both explicit and complex hidden relationships in an Active Directory environment so that Blue Teams can see what attack paths exist in their environments and limit them/clean them up before adversaries who have gained a toehold with a phishing attack can exploit them.









