The devastating compromise of an IT monitoring and management tool made by US software company SolarWinds has resulted in successful intrusions by hackers of the US Commerce and Energy departments, with the Treasury also confirmed penetrated, as US intelligence agencies scramble to contain the fallout.
The UK has also seen as-yet unnamed victims, Microsoft President Brad Smith said in an update on Redmond's own efforts to fight the attack this week. Microsoft said it has notified 40 victims in numerous countries. The company has also admitted that it was a victim: "We can confirm that we detected malicious SolarWinds binaries in our environment, which we isolated and removed" a spokesman told press this week.
Microsoft's Frank Shaw added: "We have not found evidence of access to production services or customer data."
Microsoft Azure cloud services appear to have been abused by the hackers chaining together a range of third-party vulnerabilities, the National Security Agency suggested Thursday, tellings users to lock down their systems, in the wake of the attack which is believed to have been carried out by state-sponsored attackers; most fingers have pointed at Russia.
The sweeping campaign comes weeks after the NSA warned that "Russian state-sponsored malicious cyber actors are exploiting a vulnerability in VMware ONEAccess and VMware Identity Manager products, allowing the actors access to protected data and abusing federated authentication." That particular vulnerability was tracked as CVE-2020-4006.
https://twitter.com/NSACyber/status/1339759778923474944
The attack via command injection "led to installation of a web shell and follow-on malicious activity where credentials in the form of SAML authentication assertions were generated and sent to Microsoft Active Directory Federation Services which in turn granted the actors access to protected data," the NSA said. It is being used to gain access to cloud workflows, the NSA said in a fresh update December 17 -- emphasising that this was resulting in cloud data access by the bad actors, as more details on the TTPs of alleged Russian state-sponsored actors emerged.
https://twitter.com/NSACyber/status/1340019863658618890
The agency took pains to emphasise that this was not a result of failure by Microsoft: "By abusing the federated authentication, the actors are not exploiting a vulnerability in ADFS, AD, or AAD, [Active Directory Federation Services; Active Directory; Azure Active Directory] but rather abusing the trust established across the integrated components. Due to the popularity of ADFS, numerous actors target ADFS,as well as other identity providers trusted by ADFS, to gain access to cloud services."
The NSA's Cybersecurity Advisory “Detecting Abuse of Authentication Mechanisms" and associated guidance can be found here.
SolarWinds compromise reverberates: 17,000 hit?
Reflecting the scale of the SolarWinds compromise, Microsoft President Brad Smith noted in a lengthy blog on Thursday: "Attackers installed their malware into an upgrade of [SolarWinds'] Orion product that may have been installed by more than 17,000 customers... This is not 'espionage as usual' even in the digital age," he wrote, adding that it "represents an act of recklessness that created a serious technological vulnerability for the United States and the world. In effect, this is not just an attack on specific targets, but on the trust and reliability of the world’s critical infrastructure in order to advance one nation’s intelligence agency."
Microsoft itself has been involved in the response and Smith said the company has been "working this week to notify more than 40 customers that the attackers targeted more precisely and compromised through additional and sophisticated measures." These include UK victims.
"While roughly 80% of these customers are located in the United States, this work so far has also identified victims in seven additional countries. This includes Canada and Mexico in North America; Belgium, Spain and the United Kingdom in Europe; and Israel and the UAE in the Middle East. It’s certain that the number and location of victims will keep growing" Smith said. (Microsoft's chart illustrates the campaign's targets by sector below).
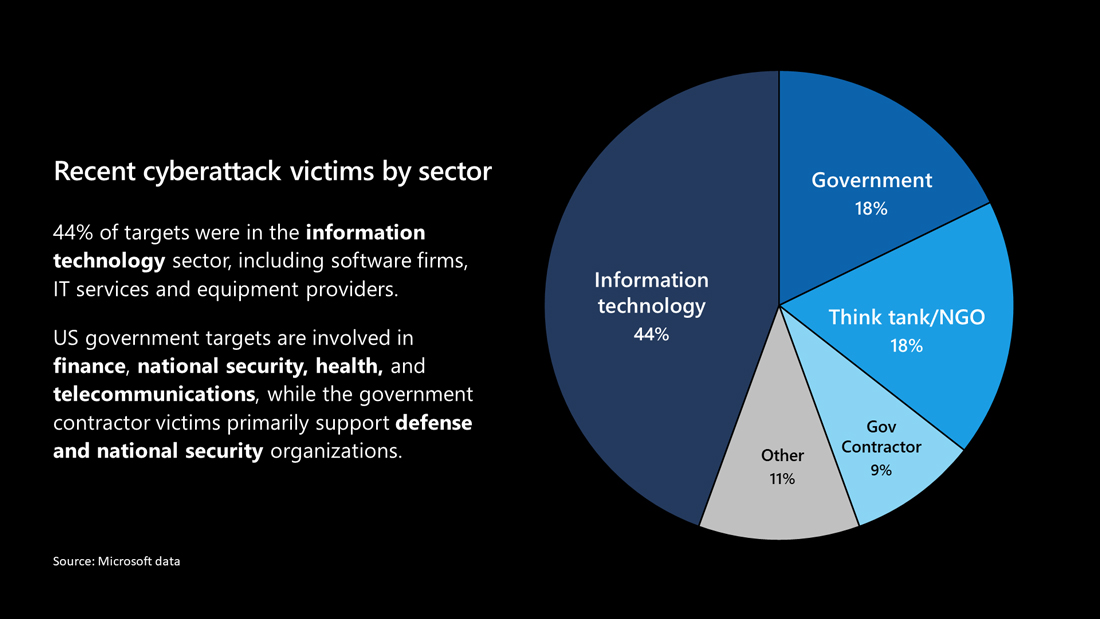
The attack was first revealed early this week by FireEye after its own compromise and confirmed by SolarWinds on Monday as a "sophisticated, manual supply chain attack" that infected firmware from March 2020. companies were still not ie
In a joint statement late Thursday, the FBI, the Cybersecurity and Infrastructure Security Agency, and the Office of the Director of National Intelligence said they were marshalling "all of the Intelligence Community’s relevant resources" to identify and mitigate compromises.
The FBI, CISA, and ODNI (describing it as a "significant and ongoing cybersecurity campaign) said it was "a developing situation and... we continue to work to understand the full extent of this campaign."
President-elect Joe Biden said Thursday: "My administration will make cybersecurity a top priority … and we will make dealing with this breach a top priority from the moment we take office" as shockwaves mounted.
You can check if you have an affected system with this NCSC guidance.
- Identify if you have a product from the SolarWinds Orion suite versions 2019.4 to 2020.2.1 HF1 inclusive. SolarWinds Orion suite consists of several products - for exact product versions see the SolarWinds advisory.
- If you are able to, check any internet web proxy, DNS proxy, or firewall logs for connections to the legitimate Solarwinds update site of downloads.solarwinds.com. This may help in identifying possible Orion Suite products. (Note, this will likely identify any SolarWinds products, not just the Orion Suite).
- If you find any Orion Suite products on your network, then check for a file named SolarWinds.Orion.Core.BusinessLayer.dll, and generate a SHA-256 hash of the file. You can use the Powershell command Get-FileHash to do this. Upload this hash to VirusTotal and check if it is detected as malicious. If it is detected then you have a copy of SolarWinds that has maliciously added functionality. This DLL is referred to as SUNBURST by FireEye.
- Check any internet web proxy, DNS proxy or firewall logs for connections to any sub-domain of avsvmcloud[.]com (which is used for command and control by the initial backdoor).
- FireEye have released multiple technical detection rules for the malicious DLL (which they call SUNBURST). If you have the ability to run these checks, then you should do so.









