Unpatched Fusion Middleware is how Oracle itself got hacked…
Read the full storyThe Stack
Interviews, insight, intelligence, and exclusive events for digital leaders.
All the latest
All the latest
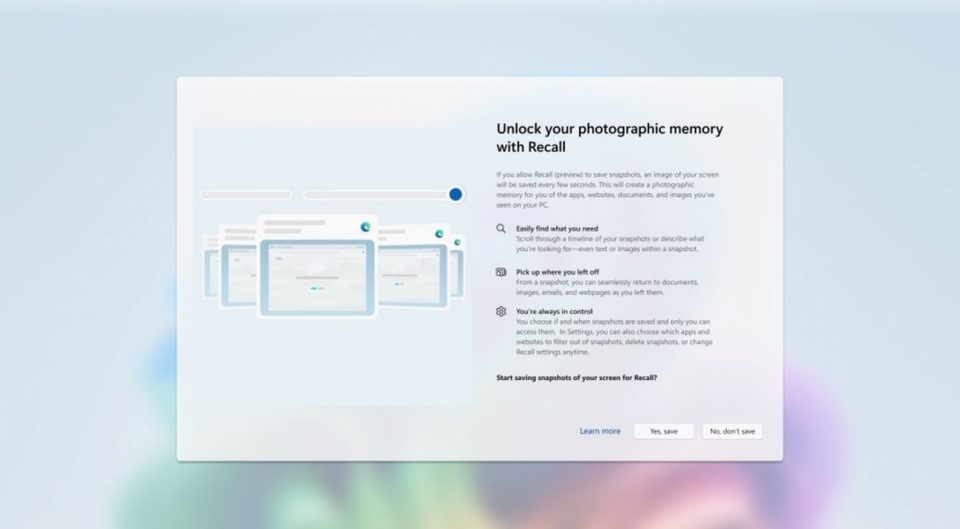
Controversial feature that sparked a firestorm of criticism is back - only this time it's allegedly built with "security and privacy in mind".

"The consultative approach and strong communication are important, but so is having the technology stack that allows quick iteration on data.”

National Security Agency joins with Five Eyes partners to issue urgent guidance on detecting and mitigating techniques that give attackers "the keys to the kingdom".

Sundar Pichai, CEO, has said the spend is "driven overwhelmingly by investment in our technical infrastructure", with the biggest cost being servers, followed by data centers.

“We have been working on fixes for the last three weeks and hope to have them available soon. We are removing support for the old CUPS browse protocol completely”
"It generates superhuman or comparable chip layouts in hours, rather than taking weeks or months of human effort."

Some 300,000 endpoints may be publicly exposed to RCE, but these are likely to be largely desktops not servers.

An attacker would need to craft a malicious container and run it "either directly (for example in services allowing shared GPU resources) or indirectly through a supply chain or social engineering attack"






















